
先吐槽:应急响应狠狠做爽了,一个人、八小时、19道应急响应+取证,隔壁浙警5分钟两个一血,火眼一把梭,没有火眼的我都要做吐了。。还有那个逆天《时间线关联非常重要》,翻了两个小时流量最后几分钟死马当活马医试出来了。逆天
附件链接:https://pan.baidu.com/s/1PQNx3li7YF6Hv_FQ0QhcvQ?pwd=xabe
提取码:xabe
Misc 威胁检测与网络流量分析:
zeroshell_1
CTF-NetA一把梭,实际在HTTP流274的Referer里
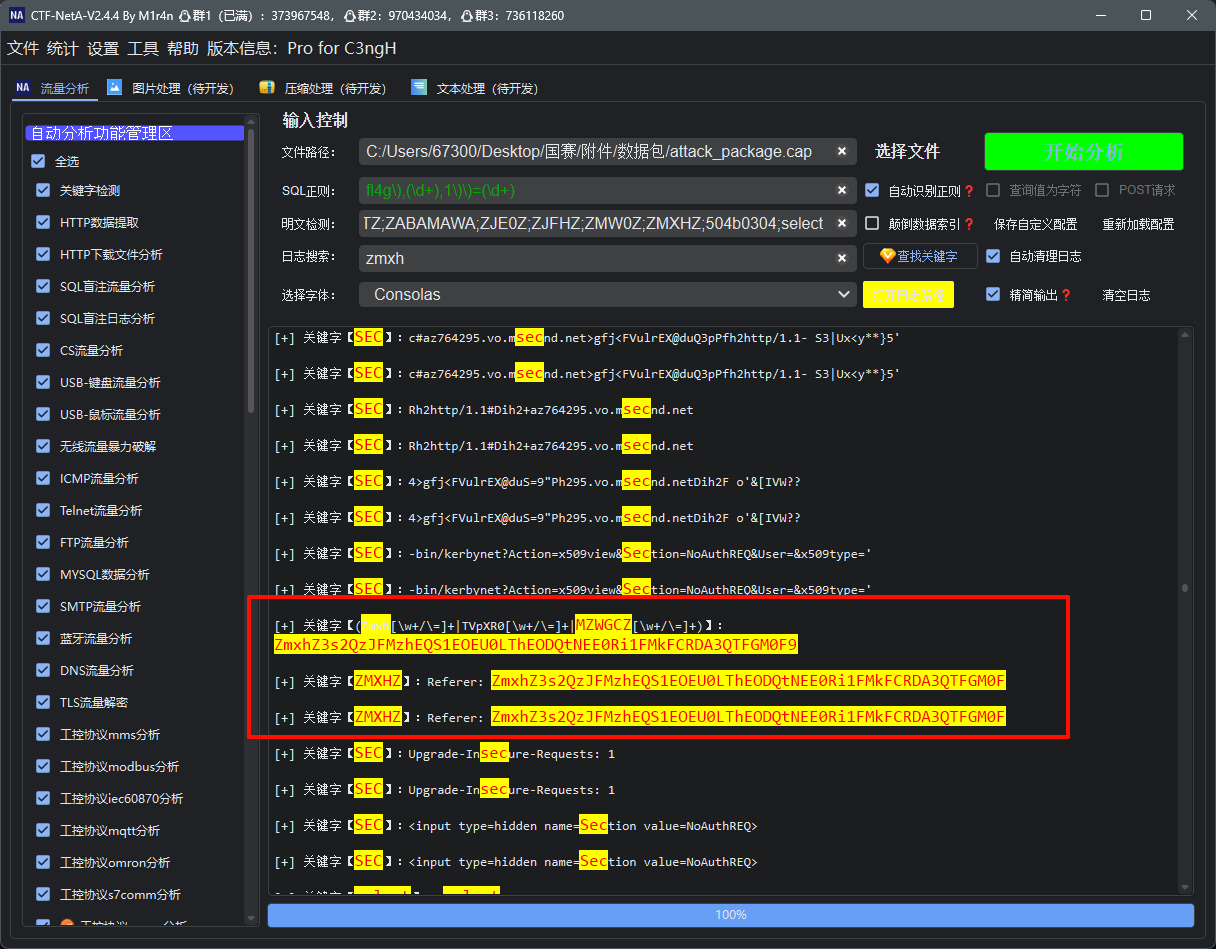
zeroshell_2
根据配置文档完成虚拟机配置后可以发现版本为3.9.0,存在CVE-2019-12725漏洞
访问路径后使用如下exp
1 | #!/usr/bin/python3.7 |
输入命令 python .\ZeroShell_RCE.py -u http://61.139.2.100/ --attack
然后输入命令find / -type f -name "*flag*"
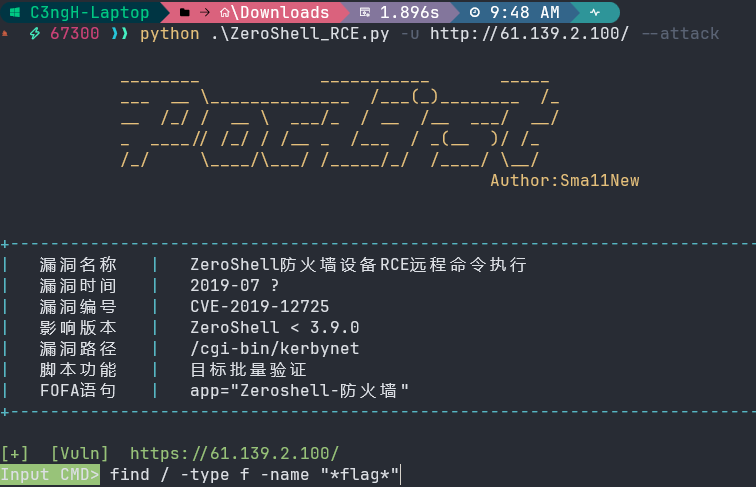
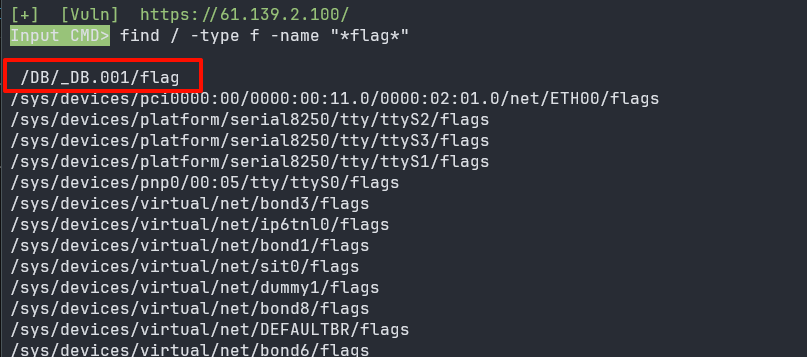
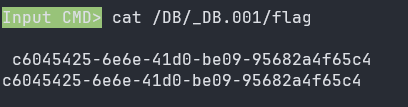
包上flag头直接提交即可
zeroshell_3
将vmdk直接使用diskgenius挂载,在第二题flag的同目录下找到一个.nginx文件,复制出来
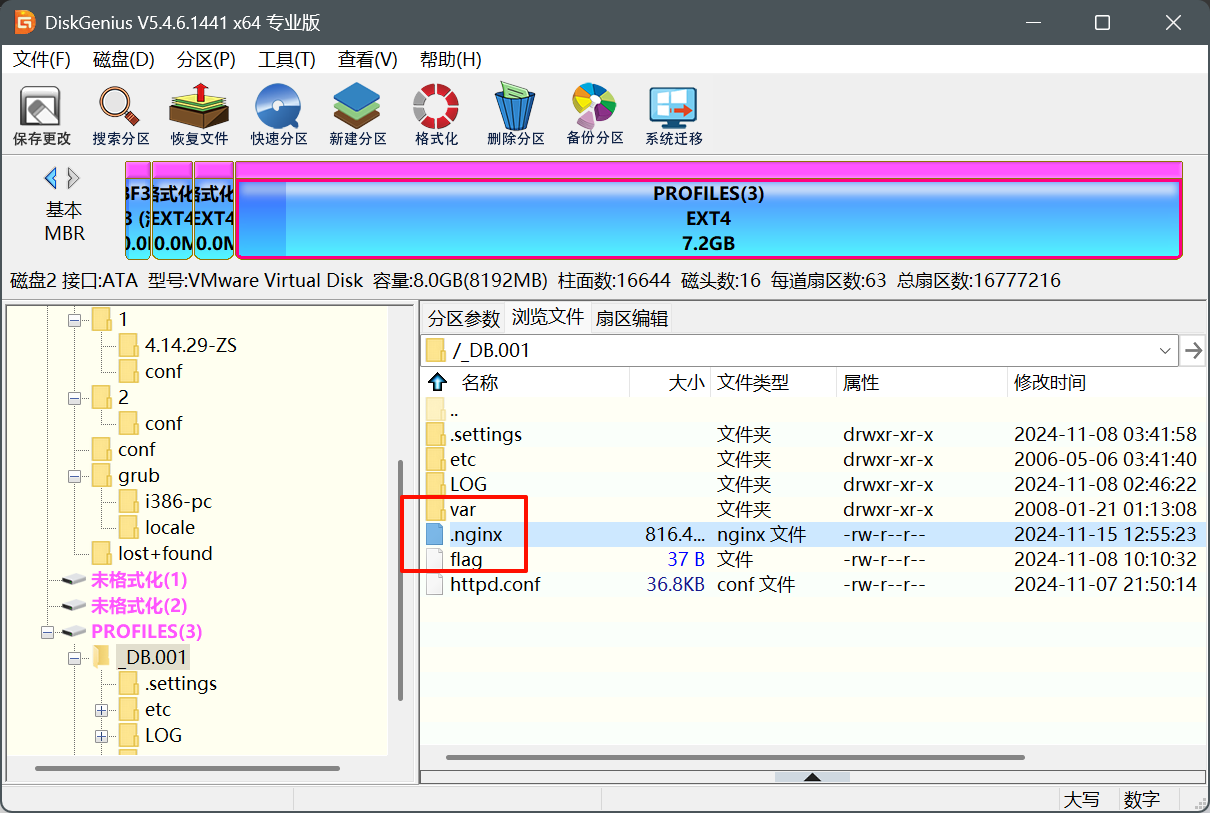
上传微步云沙箱确定是木马病毒,在静态分析的ASCII中看到一个IP地址,直接提交即可
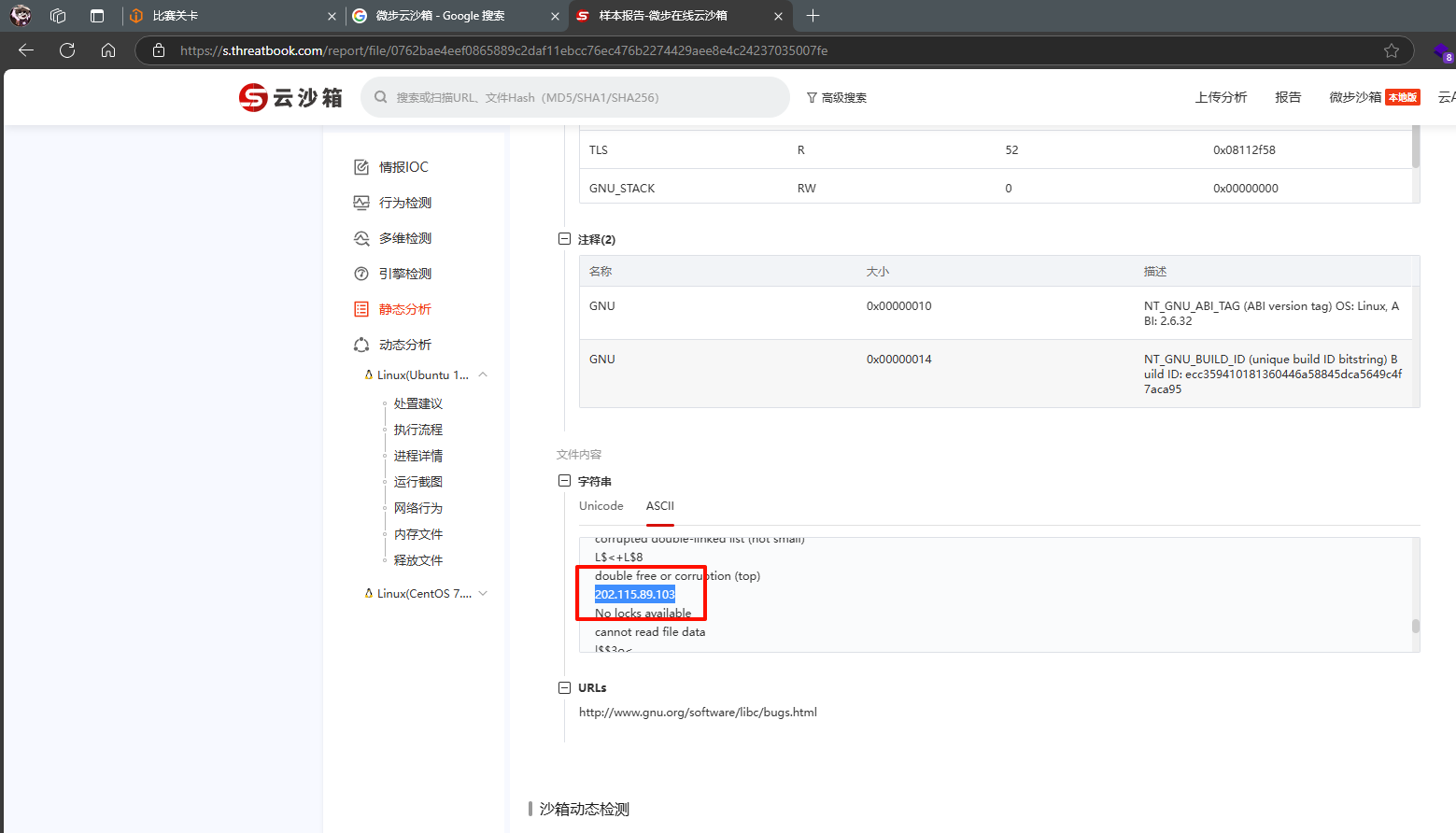
本题也可以直接使用netstat命令
zeroshell_4
第三题的文件名.nginx直接交就行
zeroshell_5
打开前一题的.nginx文件,使用ida32查看字符串发现一串可疑字符,尝试提交flag正确

WinFT_1
可以在常见的系统位置找到可疑的exe
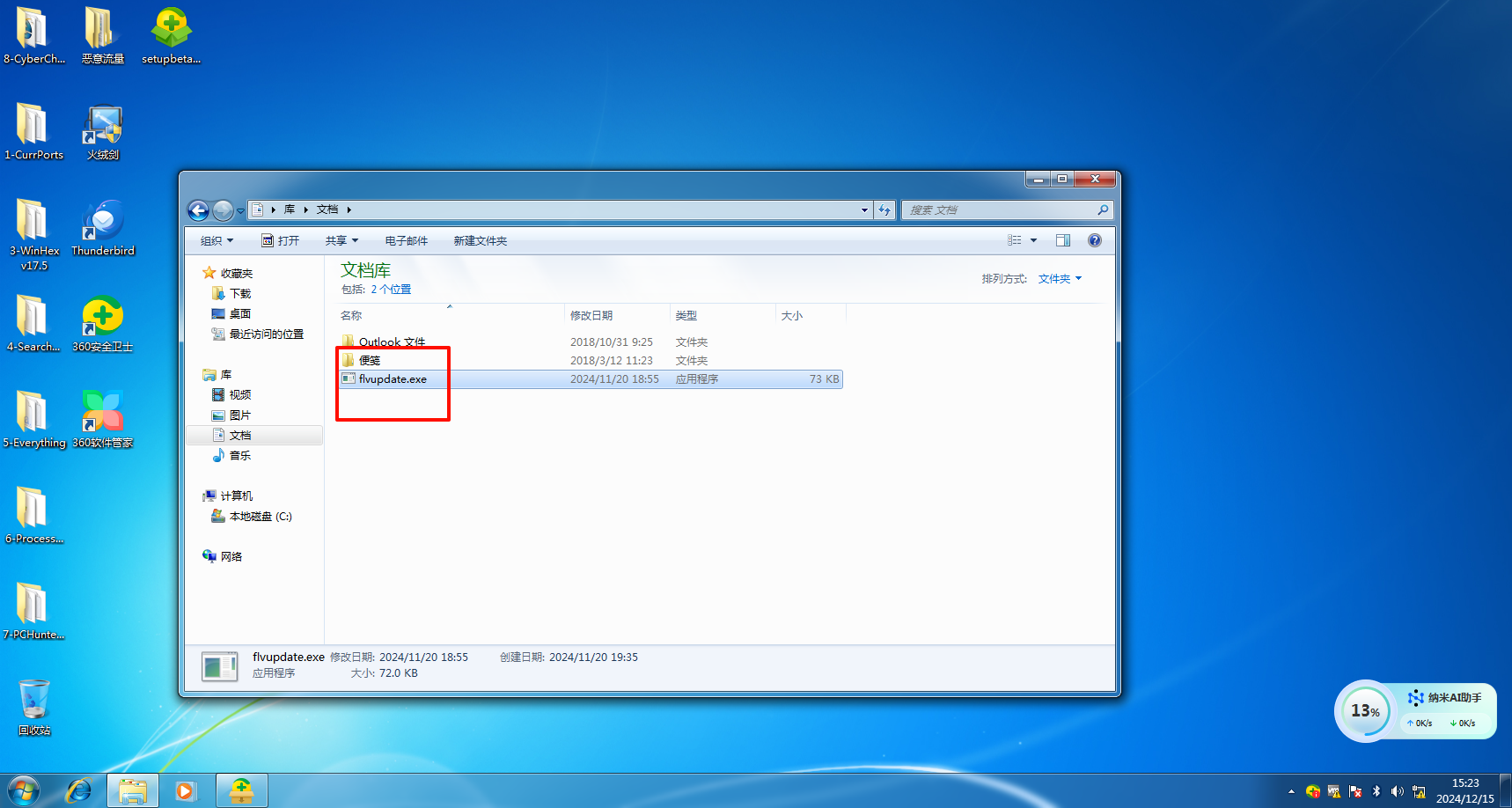
使用微步云沙箱判定为木马,在网络行为中得到域名
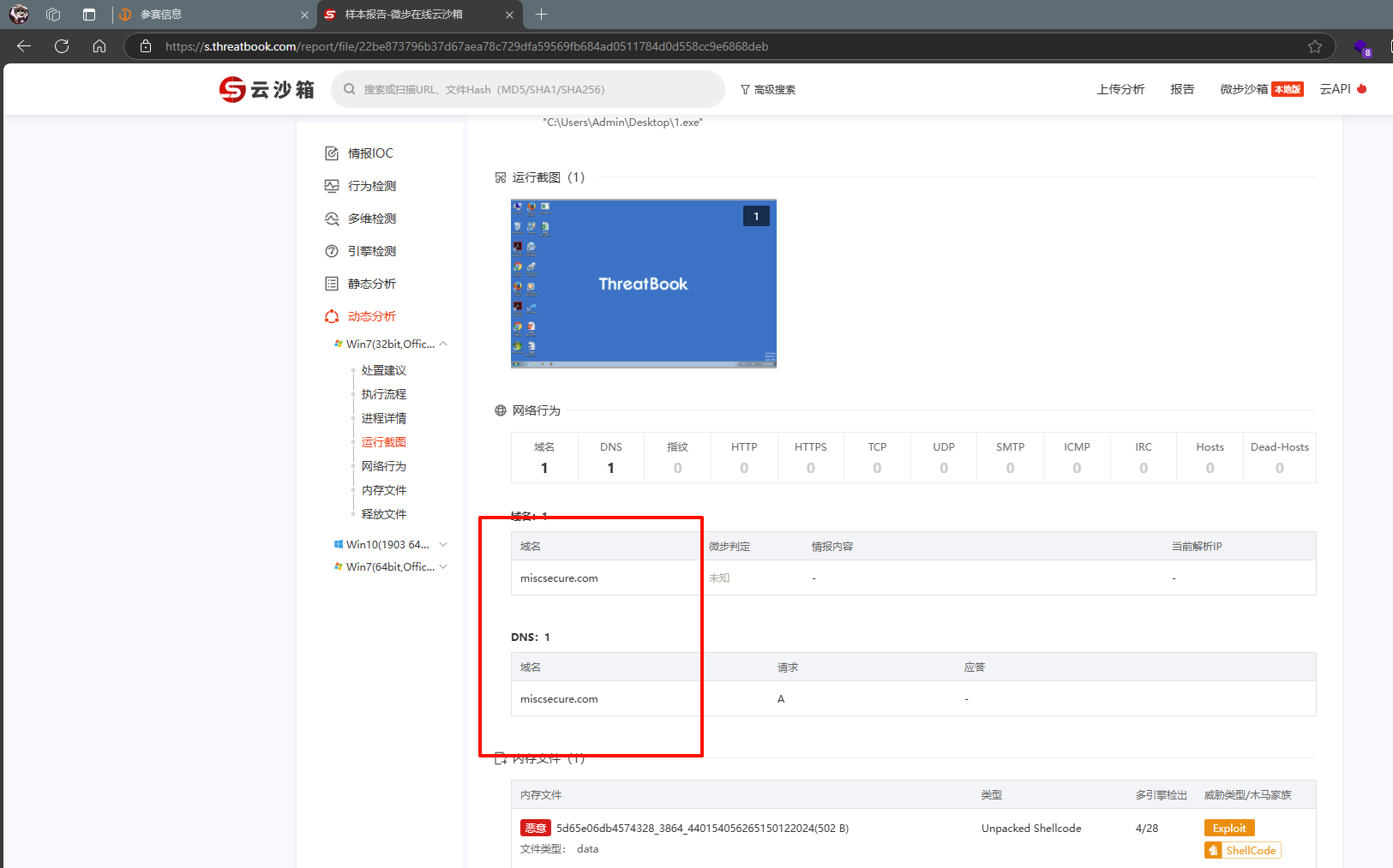
双击运行后打开桌面上的火绒剑
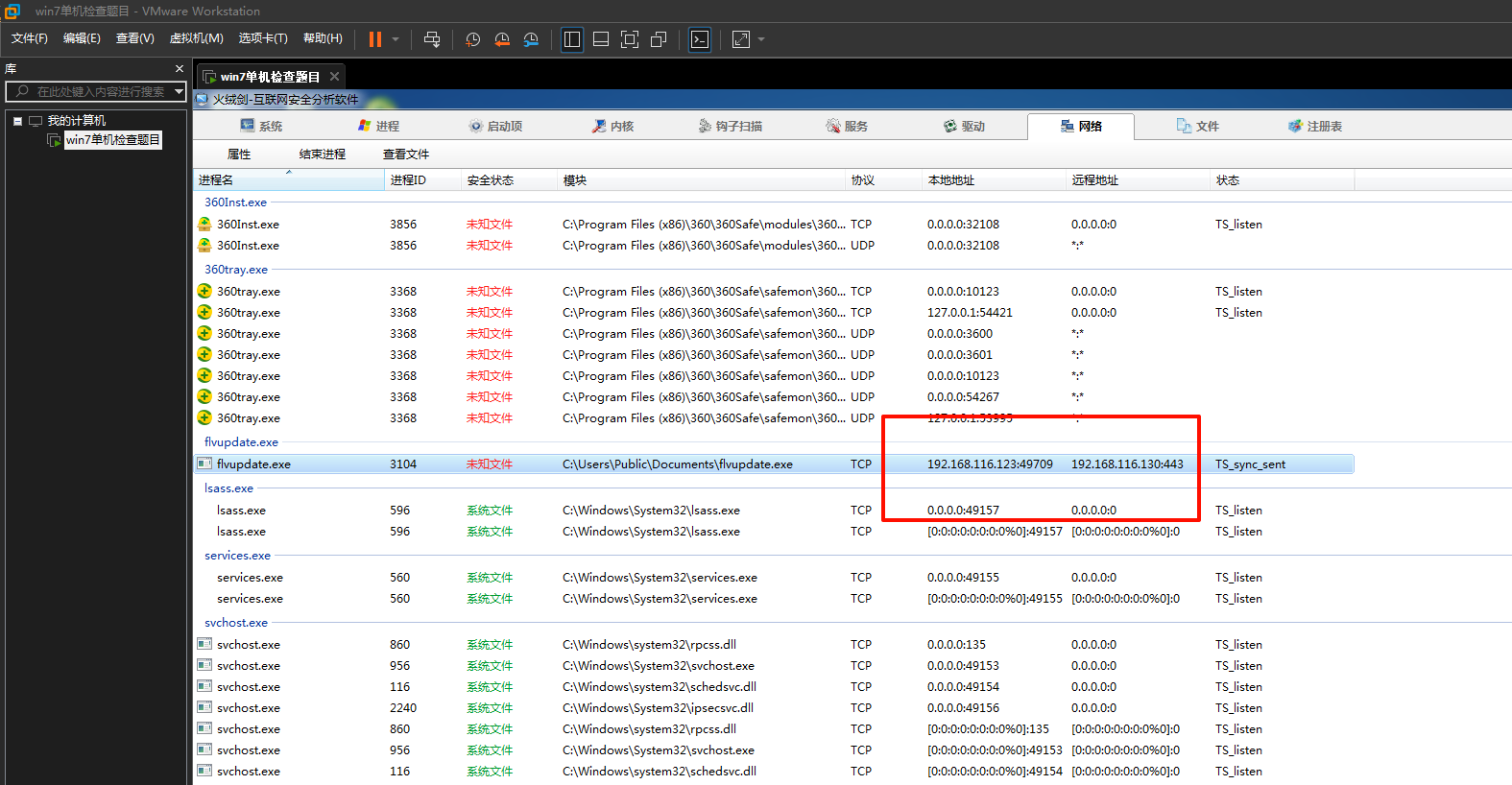
得到ip地址和端口
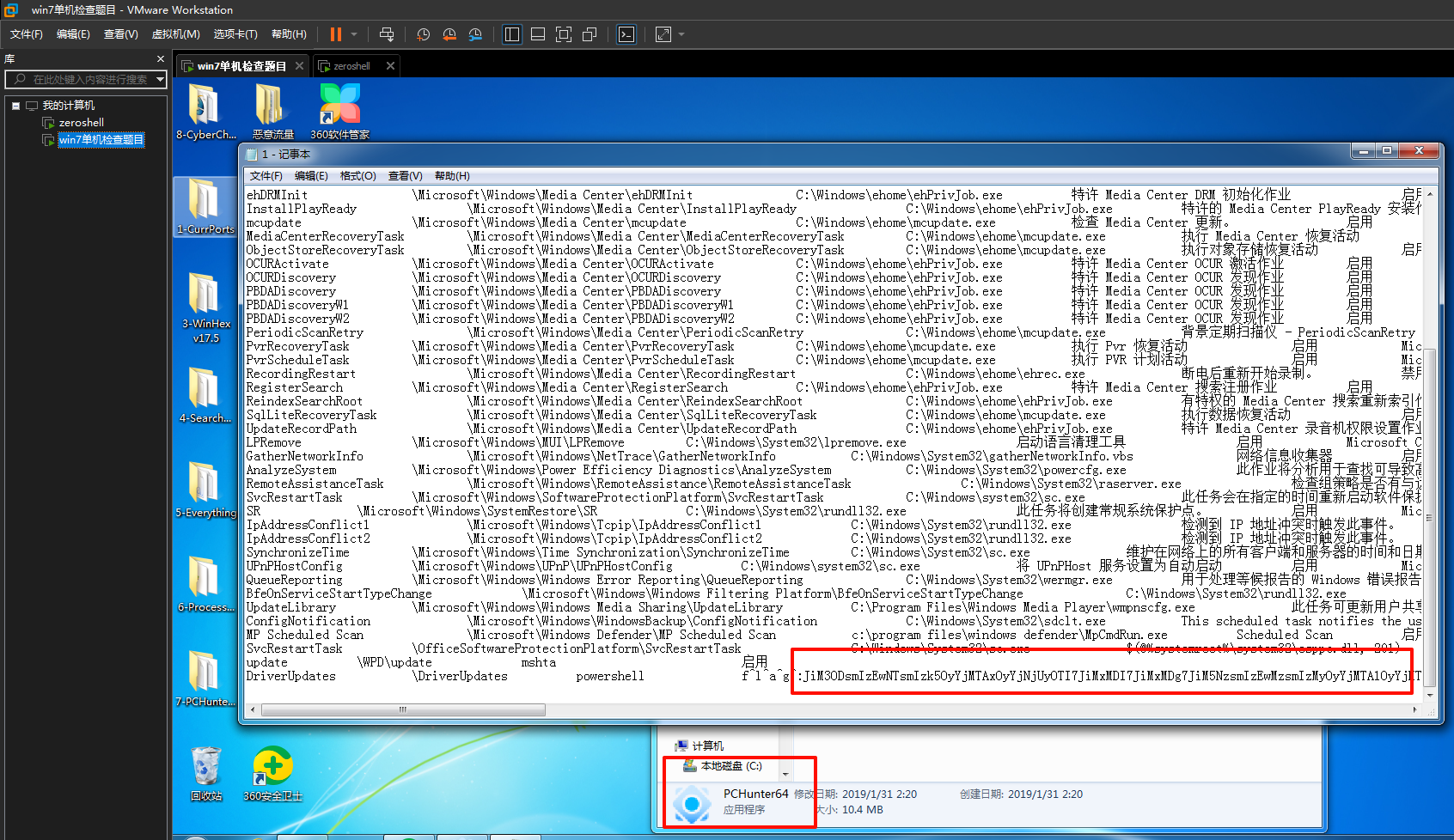
WinFT_2
使用虚拟机内的PCHunter,选择启动,第三个选项,往下拉最后一个找到flag,然后右键导出,另存为1.txt,可以发现flag密文
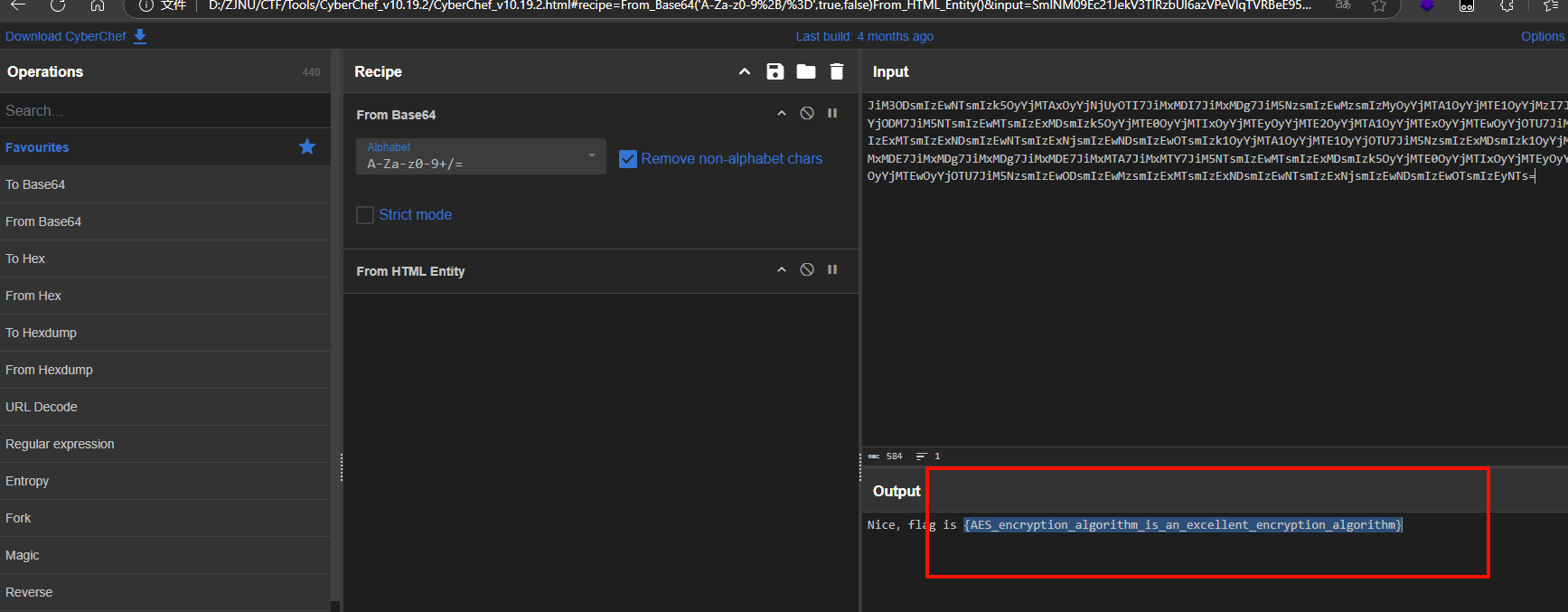
cyberchef解密得到flag
WinFT_5

CTF-NetA直接梭出压缩包,也可以导出http对象,压缩包被分为两个部分,一部分在client中,一部分在server中,修复后可不报错,但忽略报错也可进行下一步,打开发现有一个压缩包中存在flag.txt,并存在注释时间线关联非常重要

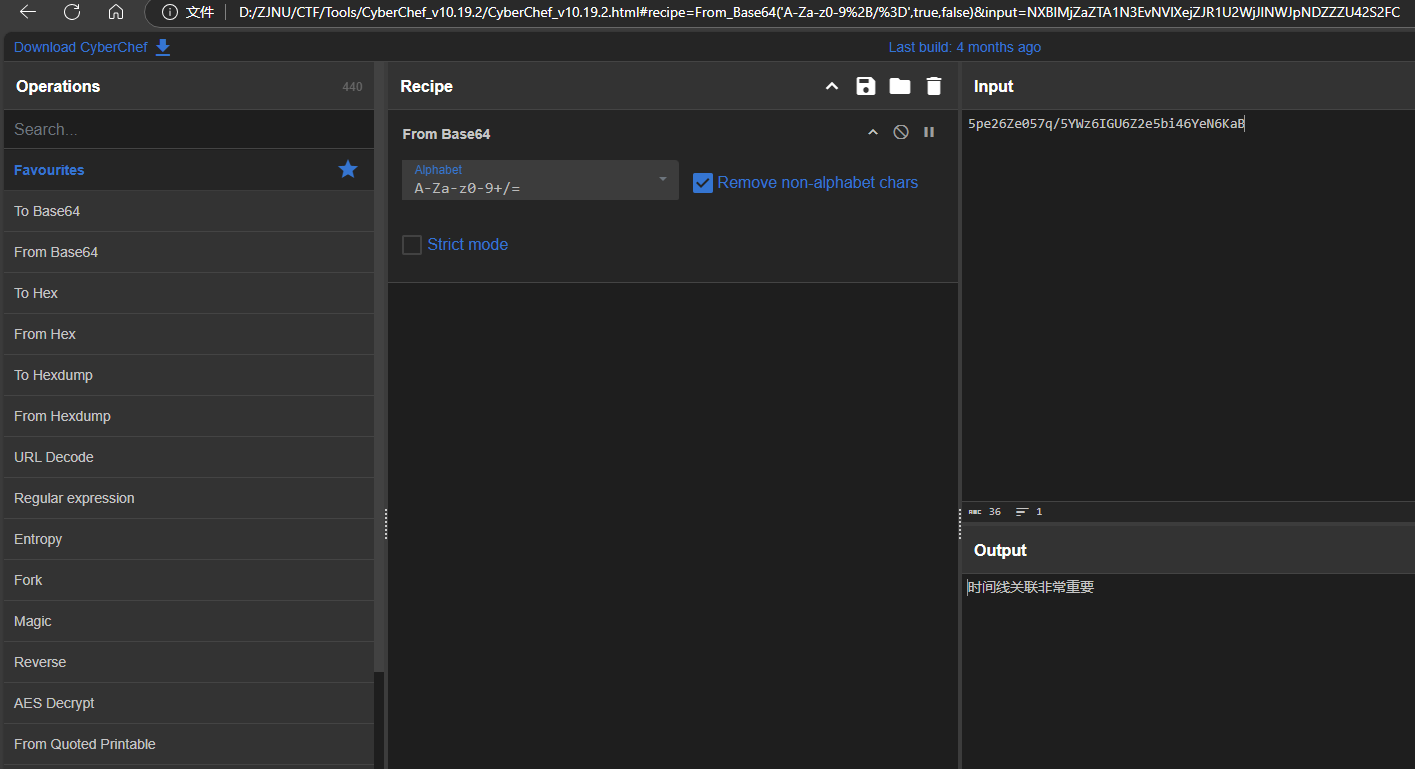
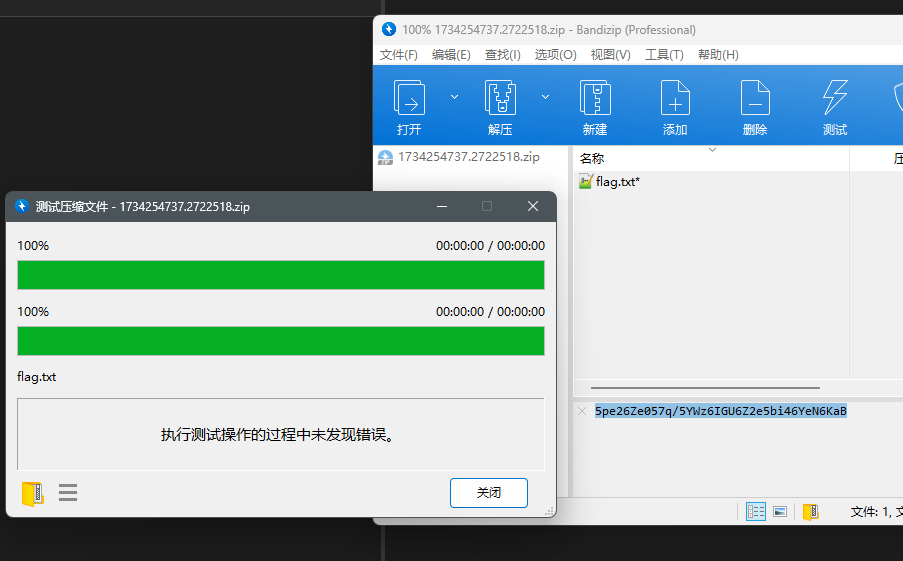 直接得到flag
直接得到flag
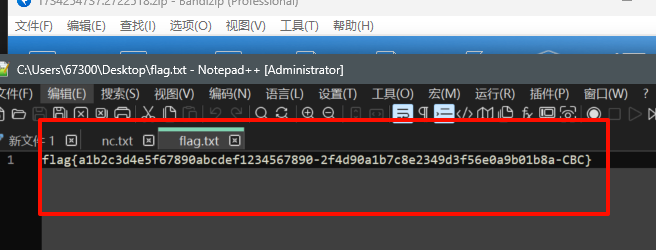
sc05_1
在excel的三张sheet中找到时间最早的,注意空格修改为下划线,转换成md5即可

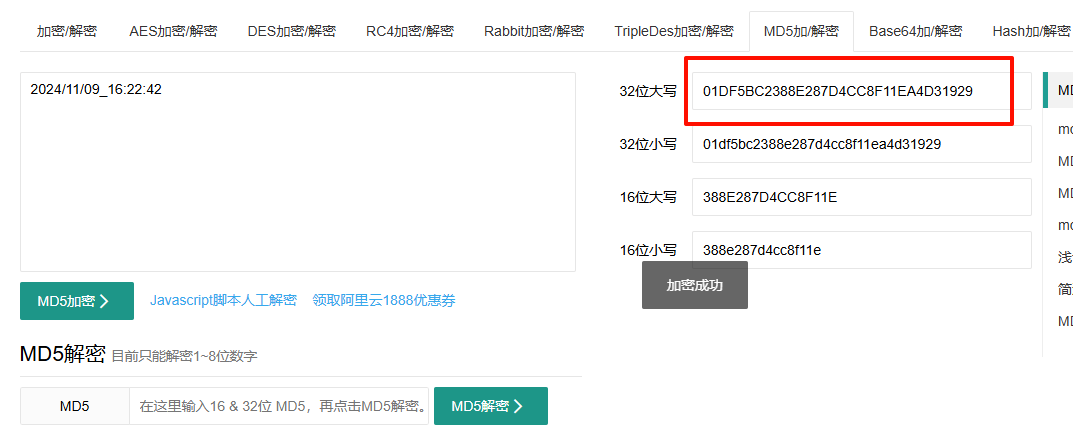
Kiwi


伪随机
1 | #include <stdint.h> |
使用hashcat跑rockyou进行爆破,包上flag头提交
1 | .\hashcat.exe -m 1000 23d1e086b85cc18587bbc8c33adefe07 .\rockyou.txt |

Crypto
rasnd
1 | ➜ 67300 nc 8.147.133.224 24638 |
1 | from Crypto.Util.number import * |
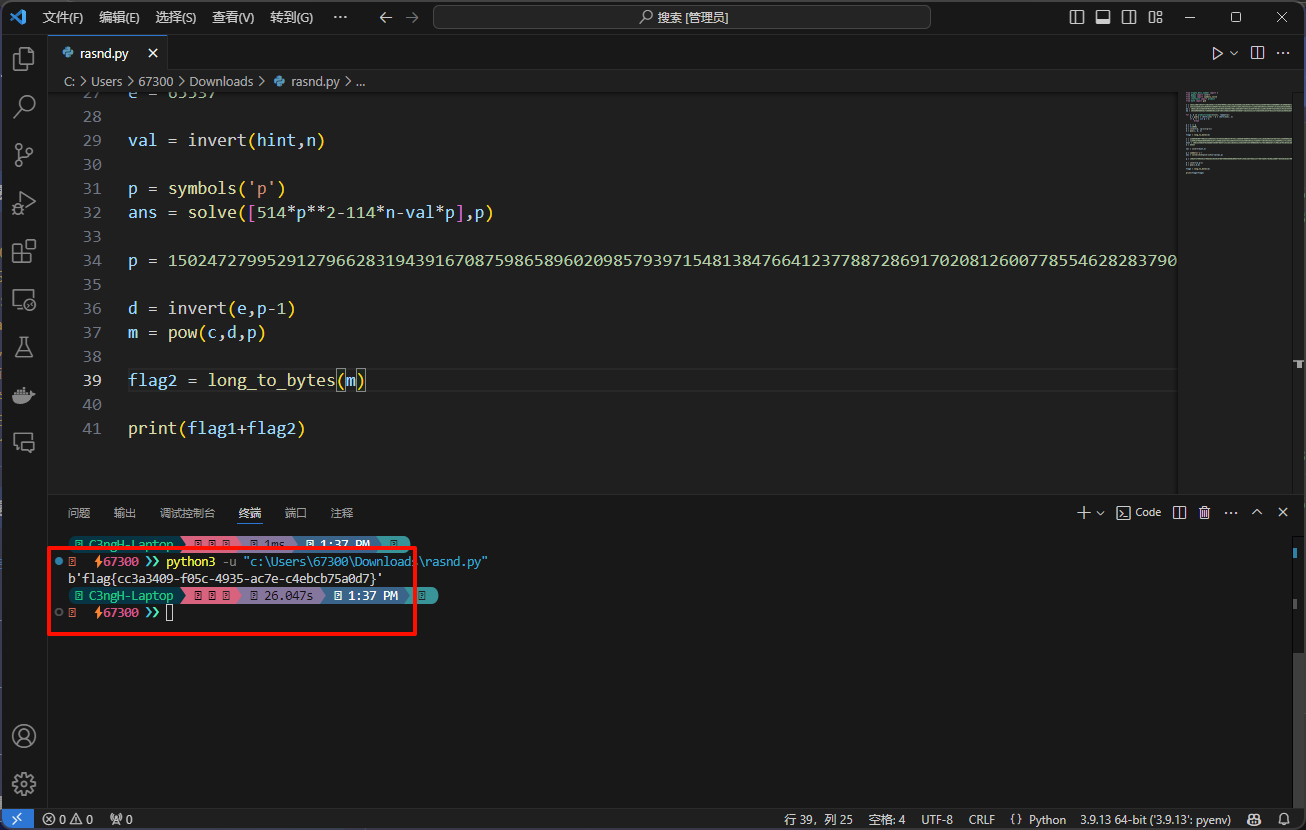
注意脚本中ans的中正的数字是下面第34行的p值