签到
第二题
1 | 6L<Ak3,*@VM*>7U&FZFNWc,Ib=t,X!+,BnSDfoaNhdiO*][5F];eV^]Lm&?$'<oeGH&6tqcgK_JDp-3;8wh?Si,G$BarTFjE?b$eR/,Igij<({u90M$5If589[<4+jp%3_%R(526#1J|m5p&H+%.#d0<DmLK*#-\8w:xD2Y[3jO{l8[)<(F[=Bcixb>Jp^%L2XvVTzW@9OTko/P74d1sFscEbMO7Vhp&HM;+ww/v[KM1%2M*7O\}rEZM.LM0'\iwK:])pg-nJef\Rt4 |
使用CyberChef:Base92 -> Base85 -> Base64 -> Base62 -> Base58 -> Base45 -> Base32
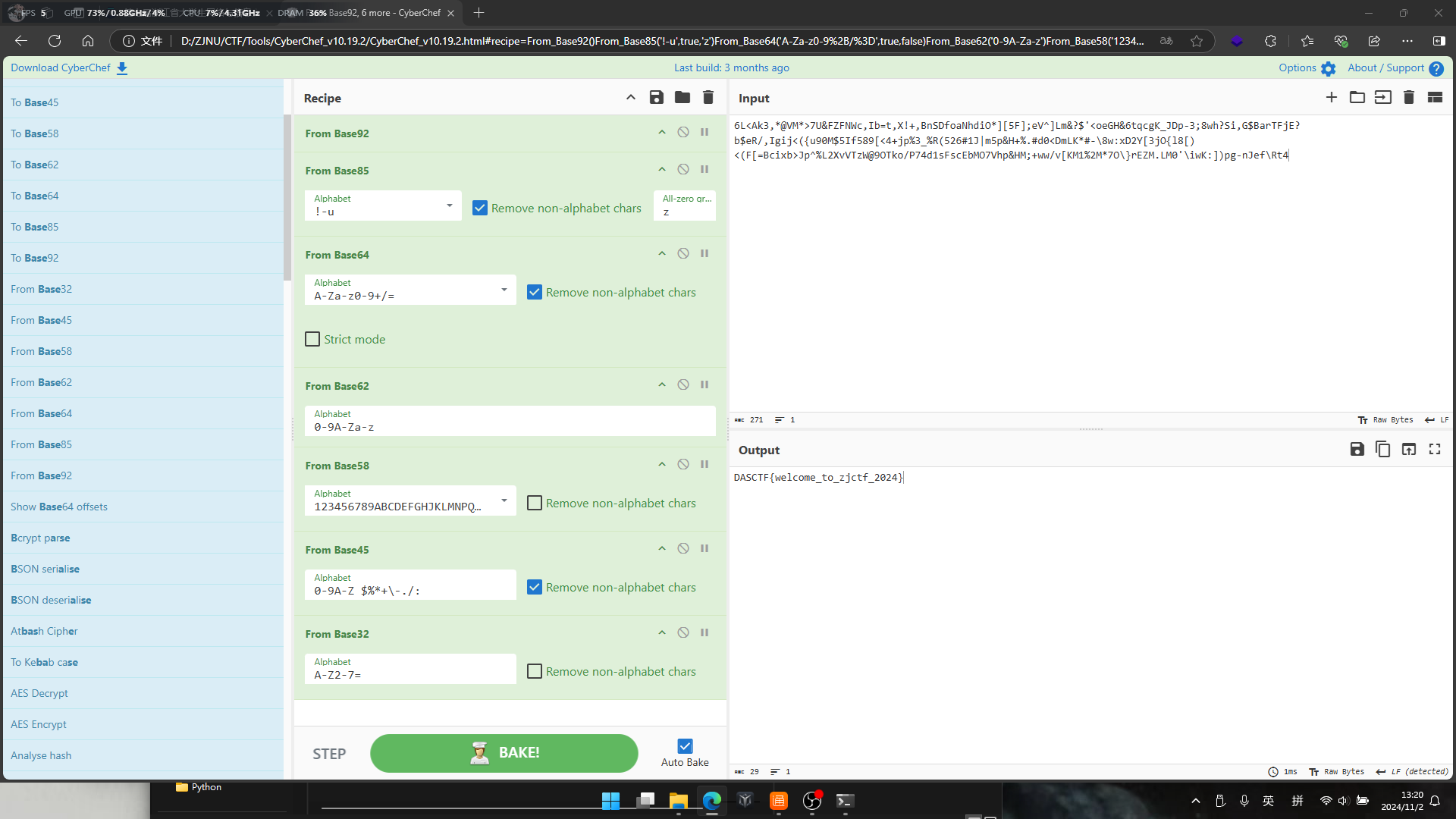
可获得flag
Misc
RealSignin
得到一张png图片,zsteg一下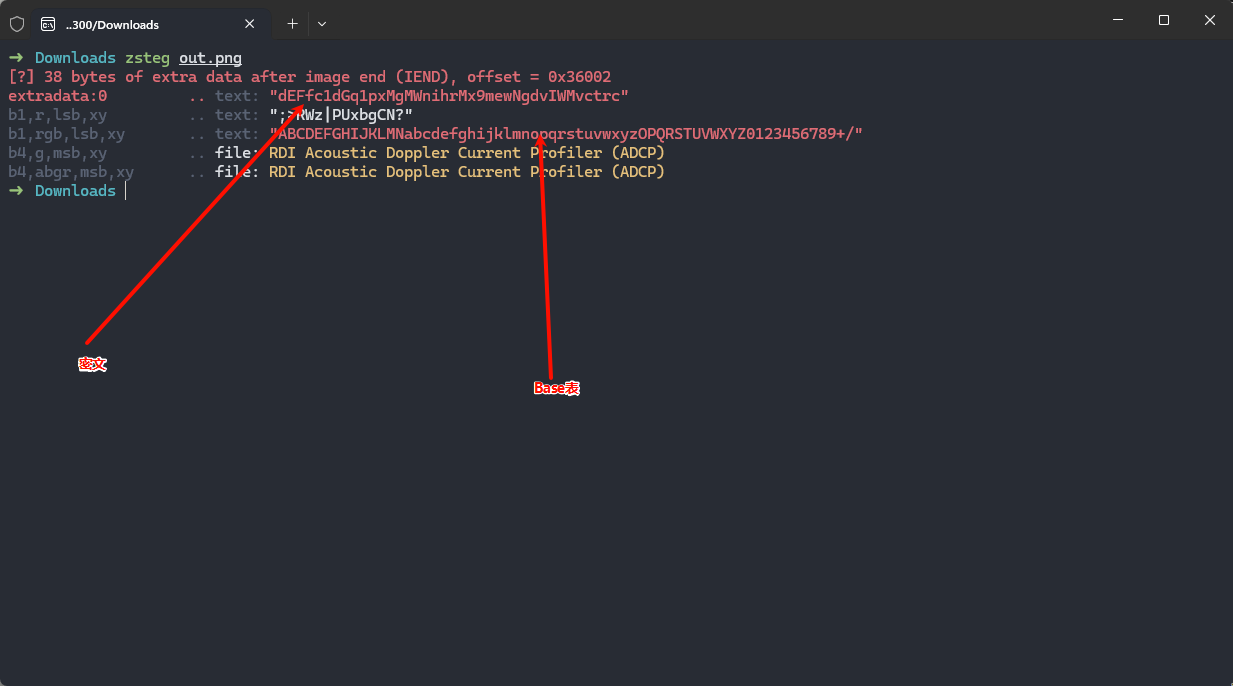
文件末尾的是密文,LSB隐写了base表
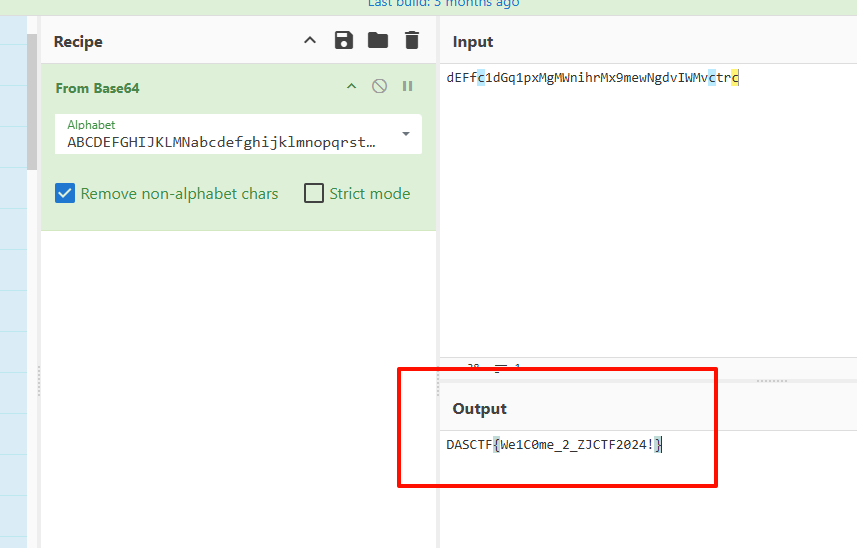
机密文档
下载后发现文件是加密的,经尝试后发现是明文攻击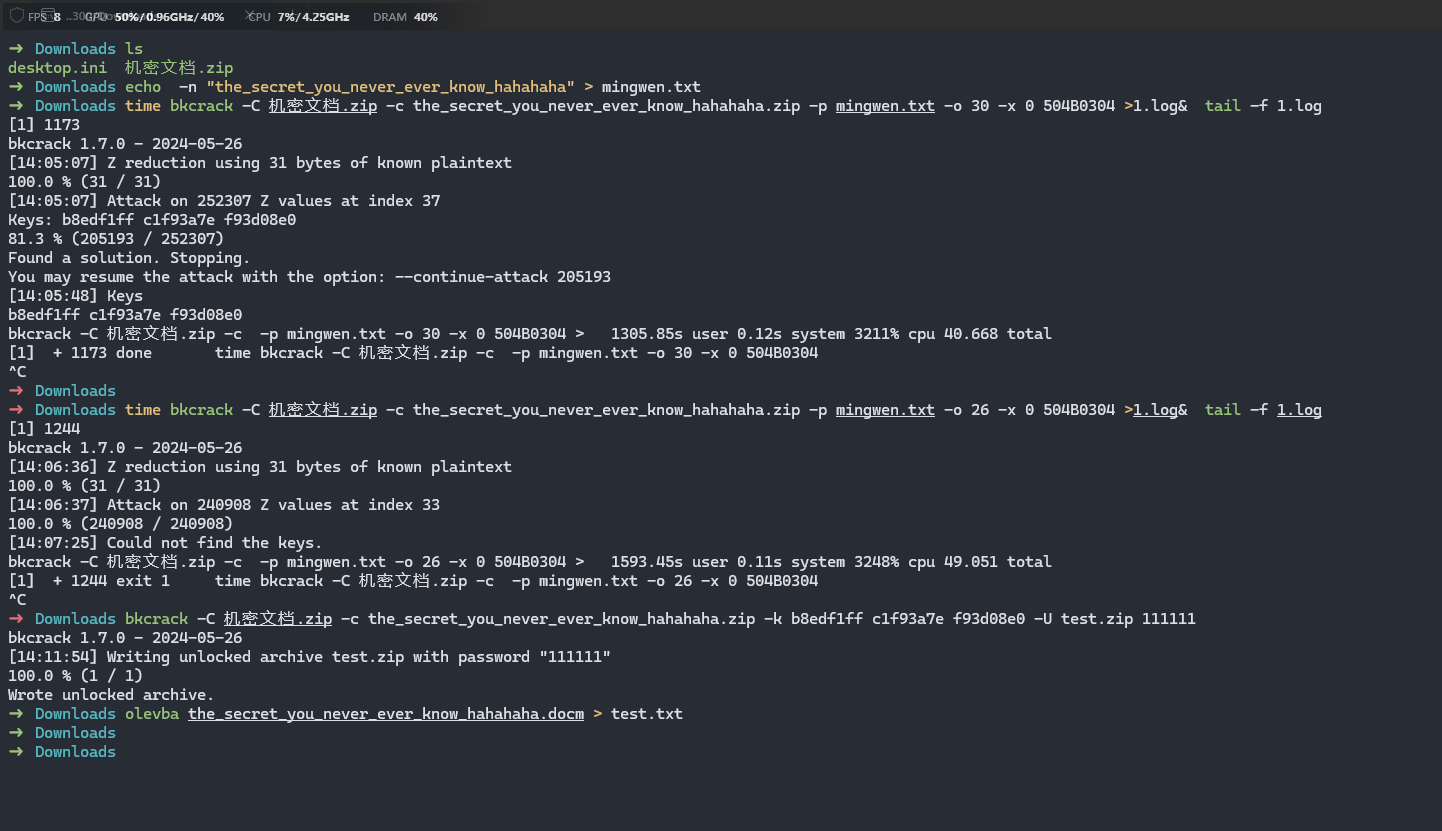
如图,使用echo -n "the_secret_you_never_ever_know_hahahaha" > mingwen.txt命令可以将内容写入mingwen.txt,这段明文已经超过8字节,加上已知的50 4B 03 04进行明文攻击,可知偏移量为30,得到如图三段密钥,然后得到密钥后使用三段密钥修改文件密码为111111,然后解压得到一个docm文件,修改后缀为zip后解压,在media文件夹内找到一张图
打开docm文件可以看到宏已被禁用
1 | olevba the_secret_you_never_ever_know_hahahaha.docm > test.txt |
可以发现一个异或的逻辑
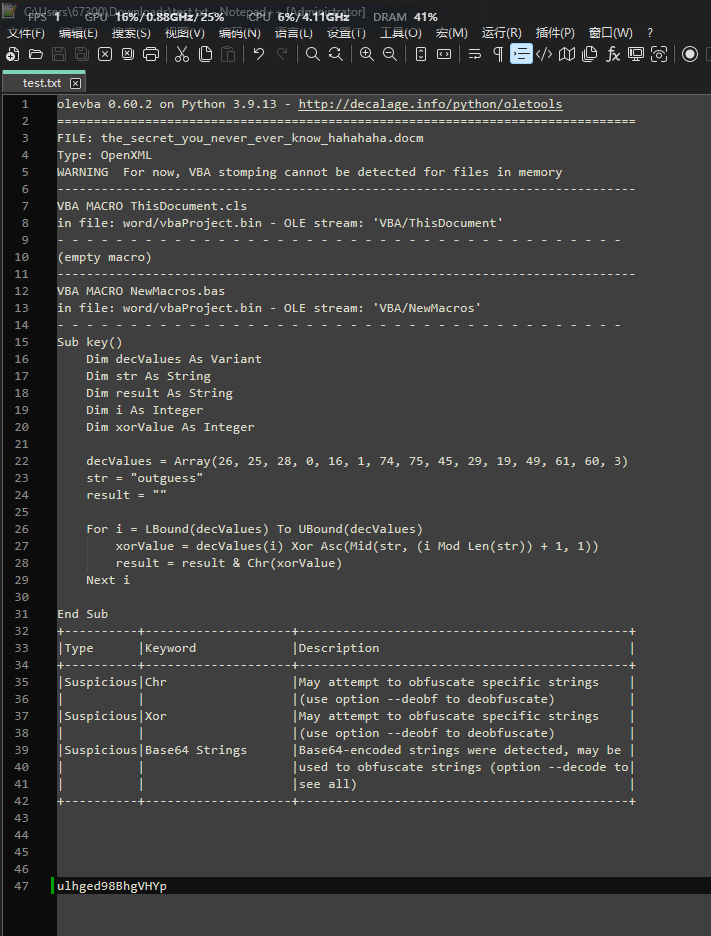
1 | data = [26, 25, 28, 0, 16, 1, 74, 75, 45, 29, 19, 49, 61, 60, 3] |
第47行为异或后的key,用它解media里的图片 outguess隐写即可
要把后缀名改成jpg
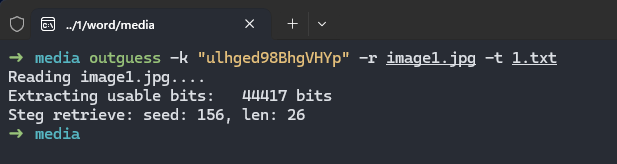
解得flag
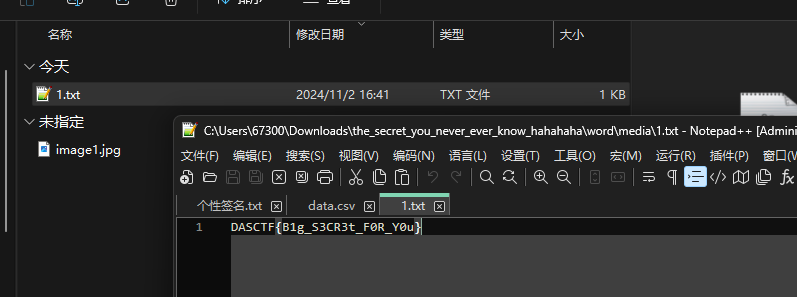
eztraffic
打开查看协议分级,发现主要为SMB流量,尝试导出SMB对象,获得final_out.zip
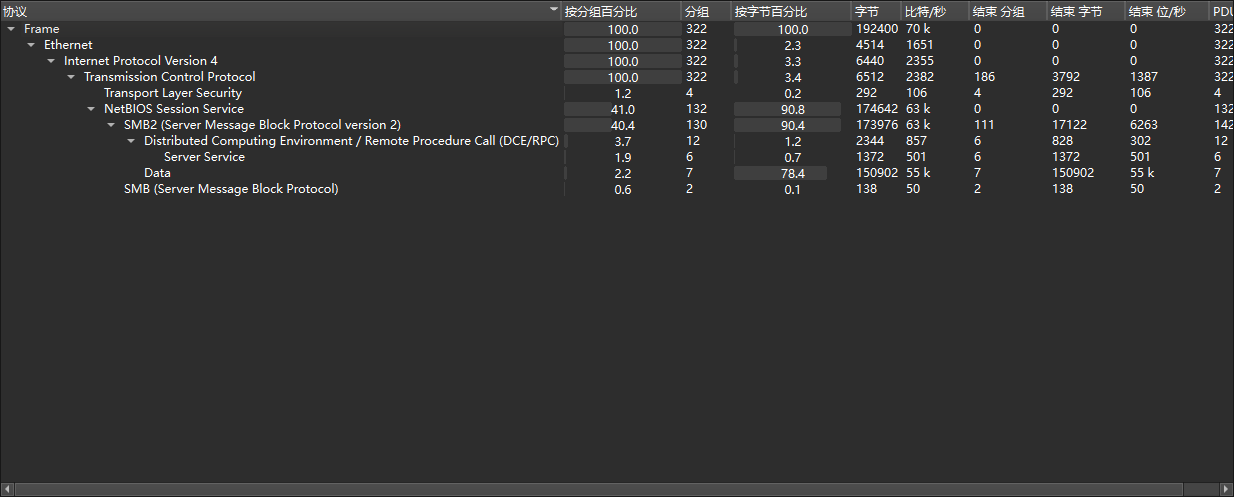
打开后看到注释
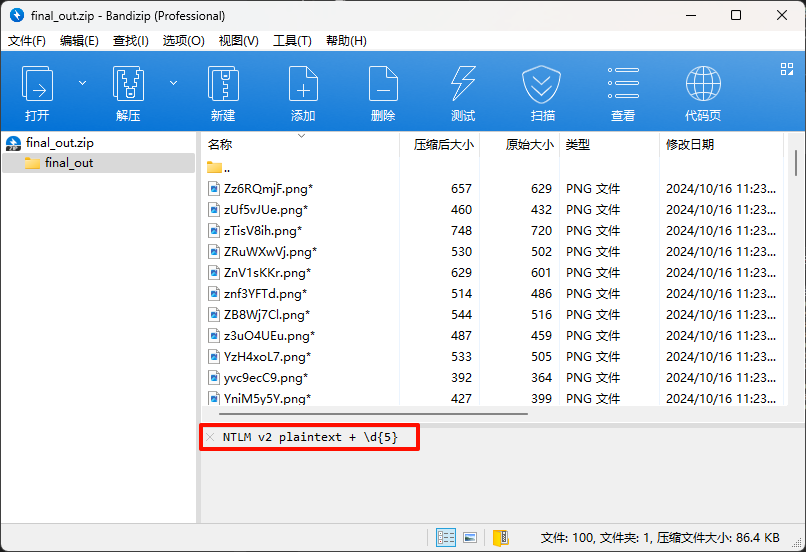
猜测是SMB协议传输的NTLM密码+五位数字掩码攻击获得flag,使用tshark导出
1 | tshark -n -r eztraffic.pcapng -Y 'ntlmssp.messagetype == 0x00000003' -T fields -e ntlmssp.auth.username -e ntlmssp.auth.domain -e ntlmssp.ntlmv2_response.ntproofstr -e ntlmssp.auth.sesskey -e smb2.sesid |
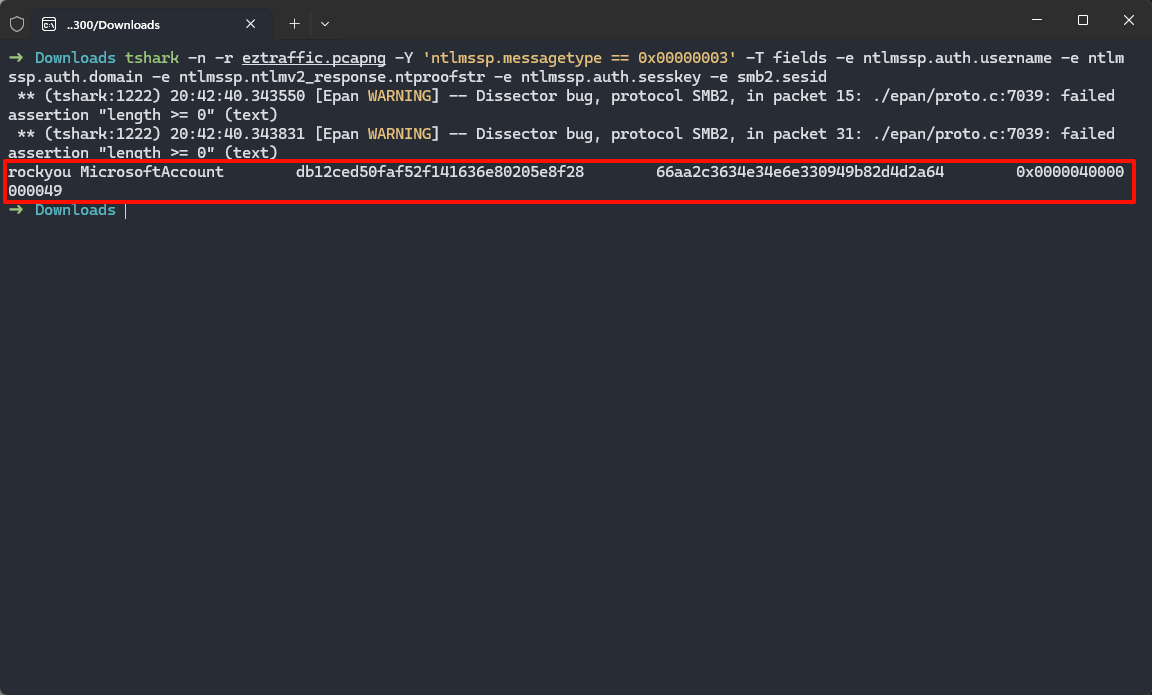
1 | username::domain:ServerChallenge:NTproofstring:modifiedntlmv2response |
1 | hashcat -m 5600 hash.txt rockyou.txt |
得到密码haticehatice,并进行掩码攻击
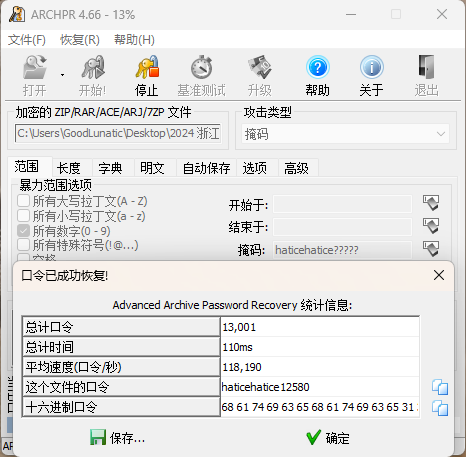
得到解压密码后获得100张图片,在每张图片的Red 0通道中找到一张隐写的二维码,扫描二维码得到该图片在拼图中的顺序,写脚本完成拼图
1 | from PIL import Image |


