签到
第二题
1
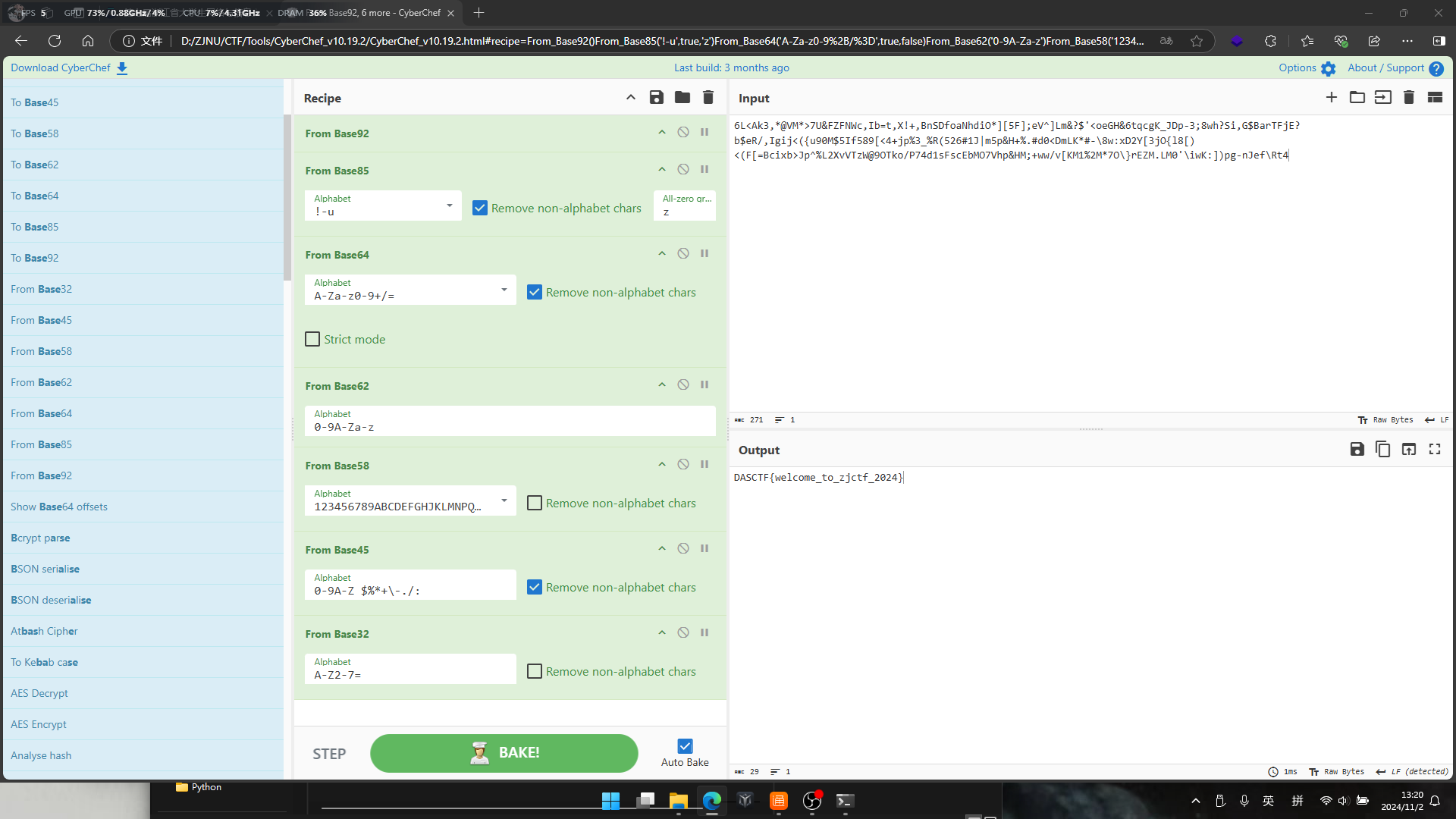
| 6L<Ak3,*@VM*>7U&FZFNWc,Ib=t,X!+,BnSDfoaNhdiO*][5F];eV^]Lm&?$'<oeGH&6tqcgK_JDp-3;8wh?Si,G$BarTFjE?b$eR/,Igij<({u90M$5If589[<4+jp%3_%R(526#1J|m5p&H+%.#d0<DmLK*#-\8w:xD2Y[3jO{l8[)<(F[=Bcixb>Jp^%L2XvVTzW@9OTko/P74d1sFscEbMO7Vhp&HM;+ww/v[KM1%2M*7O\}rEZM.LM0'\iwK:])pg-nJef\Rt4
|
使用CyberChef:Base92 -> Base85 -> Base64 -> Base62 -> Base58 -> Base45 -> Base32
![image]()
可获得flag
Misc
RealSignin
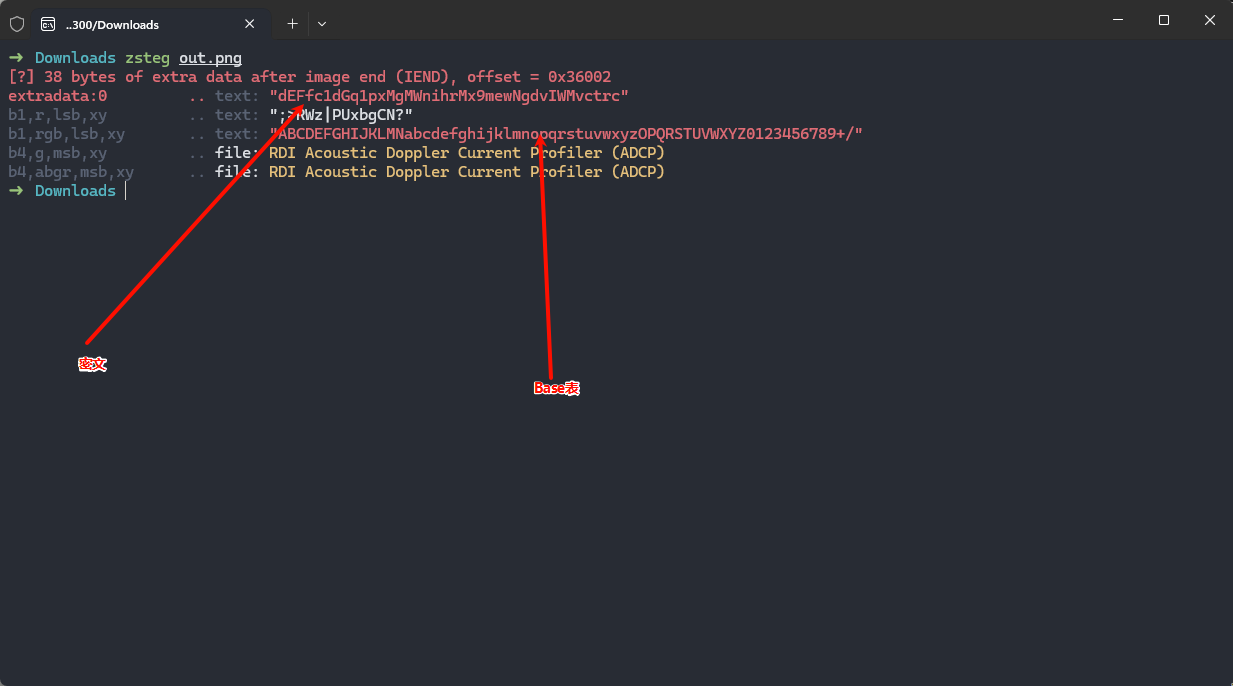
得到一张png图片,zsteg一下![image]()
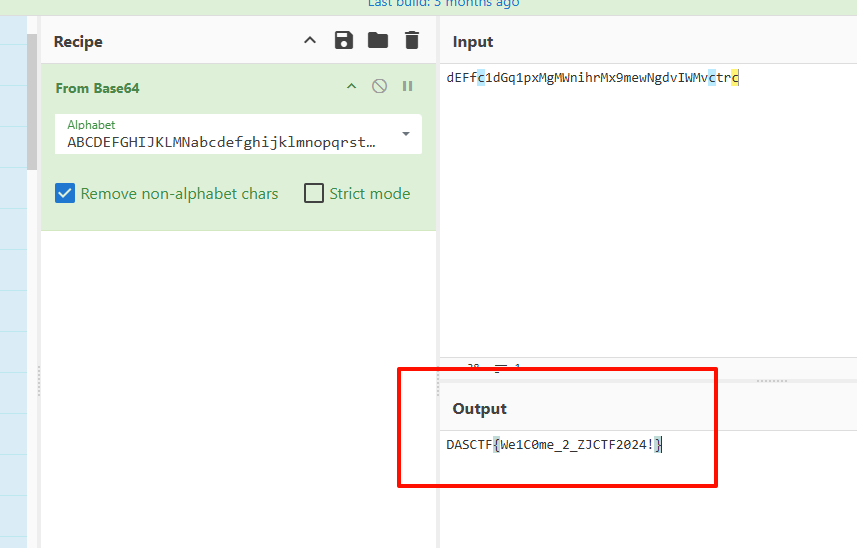
文件末尾的是密文,LSB隐写了base表
![image]()
机密文档
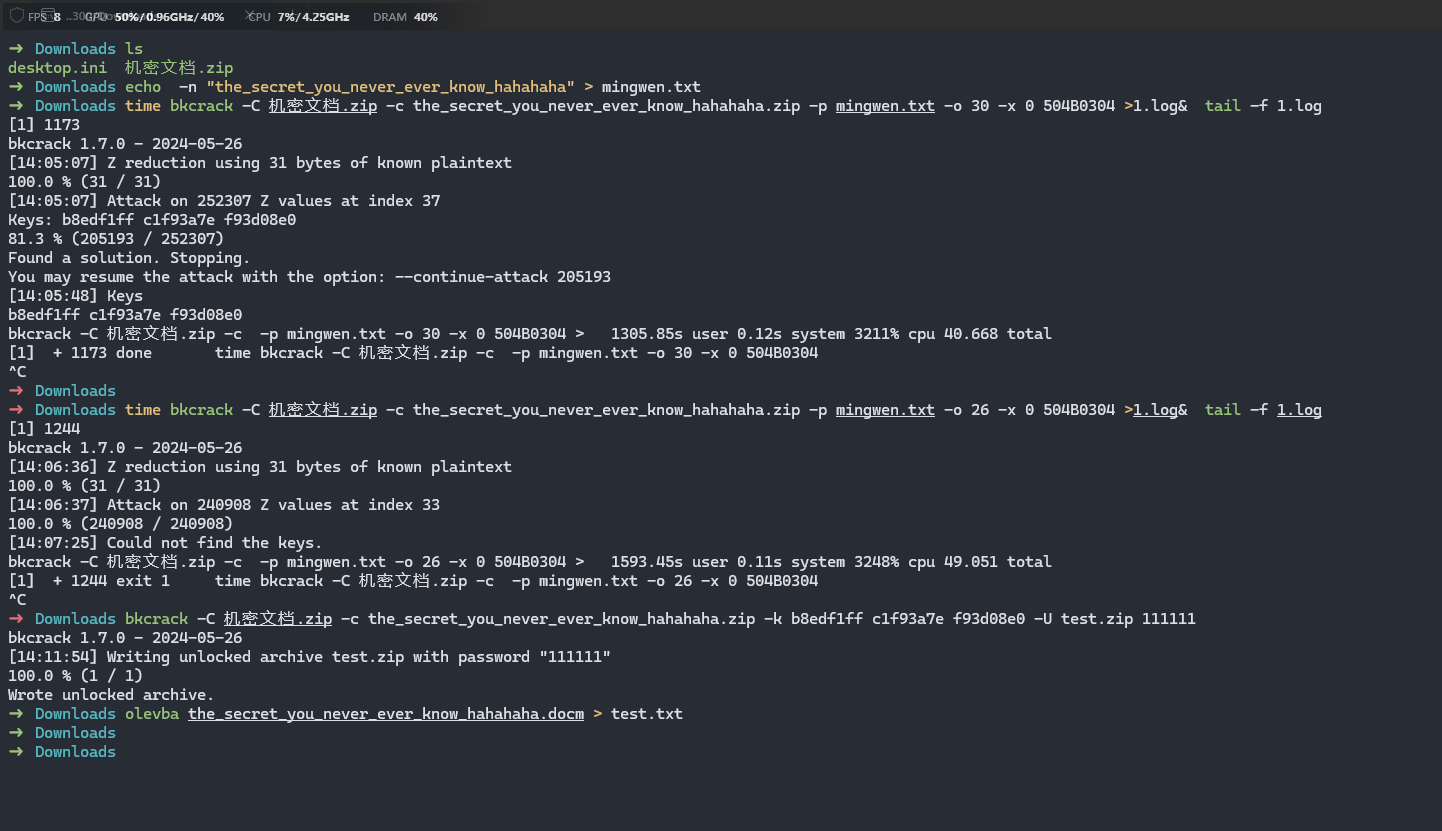
下载后发现文件是加密的,经尝试后发现是明文攻击![image]()
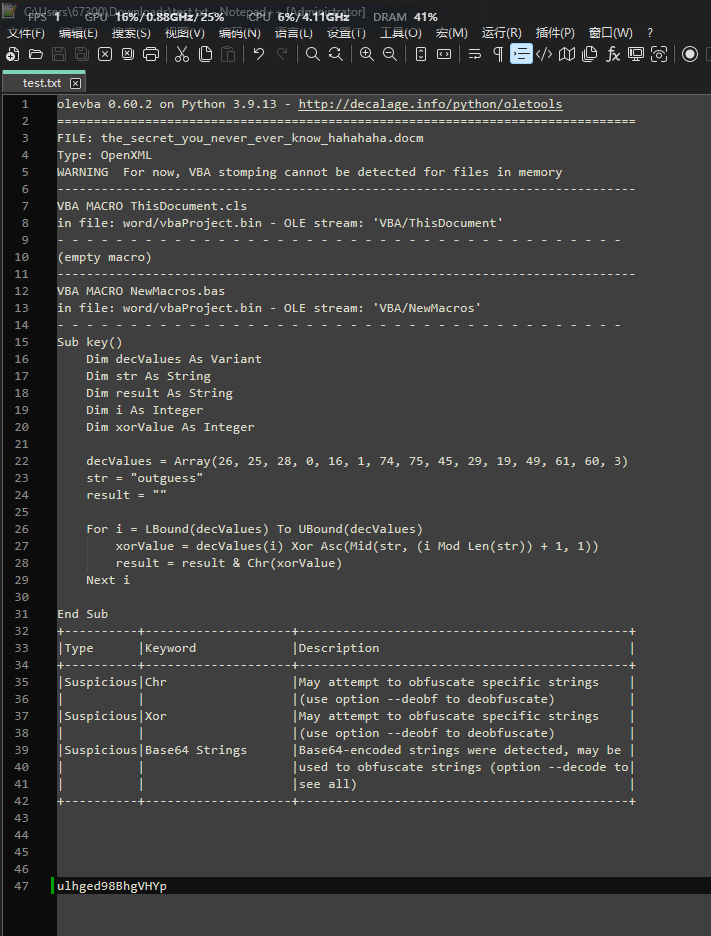
如图,使用echo -n "the_secret_you_never_ever_know_hahahaha" > mingwen.txt命令可以将内容写入mingwen.txt,这段明文已经超过8字节,加上已知的50 4B 03 04进行明文攻击,可知偏移量为30,得到如图三段密钥,然后得到密钥后使用三段密钥修改文件密码为111111,然后解压得到一个docm文件,修改后缀为zip后解压,在media文件夹内找到一张图
打开docm文件可以看到宏已被禁用
1
| olevba the_secret_you_never_ever_know_hahahaha.docm > test.txt
|
可以发现一个异或的逻辑
![image]()
1
2
3
4
5
6
| data = [26, 25, 28, 0, 16, 1, 74, 75, 45, 29, 19, 49, 61, 60, 3]
key = "outguess"
key_len = len(key)
for i in range(len(data)):
tmp = data[i] ^ ord(key[(i % key_len)])
print(chr(tmp),end='')
|
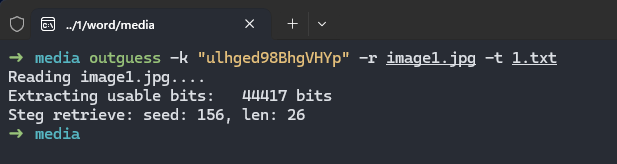
第47行为异或后的key,用它解media里的图片 outguess隐写即可
要把后缀名改成jpg
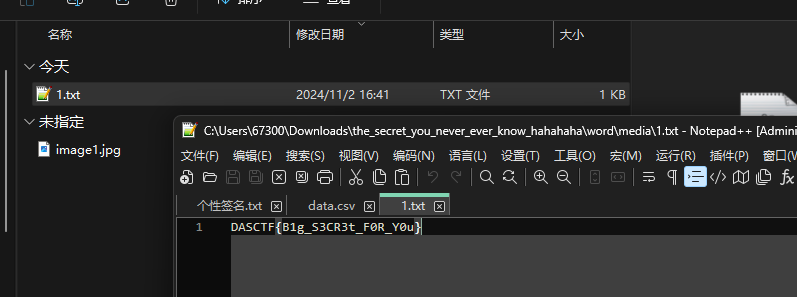
![image]()
解得flag
![image]()
eztraffic
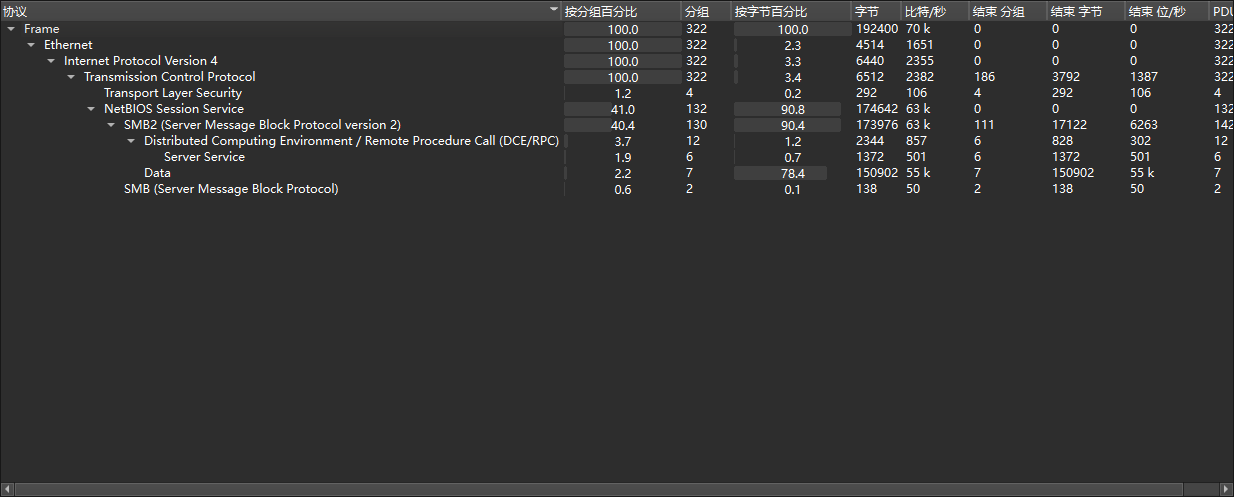
打开查看协议分级,发现主要为SMB流量,尝试导出SMB对象,获得final_out.zip
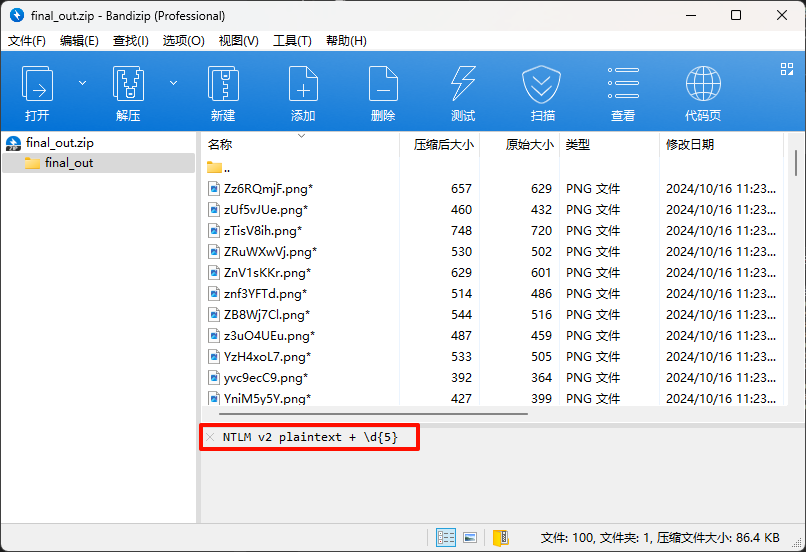
![image]()
打开后看到注释
![image]()
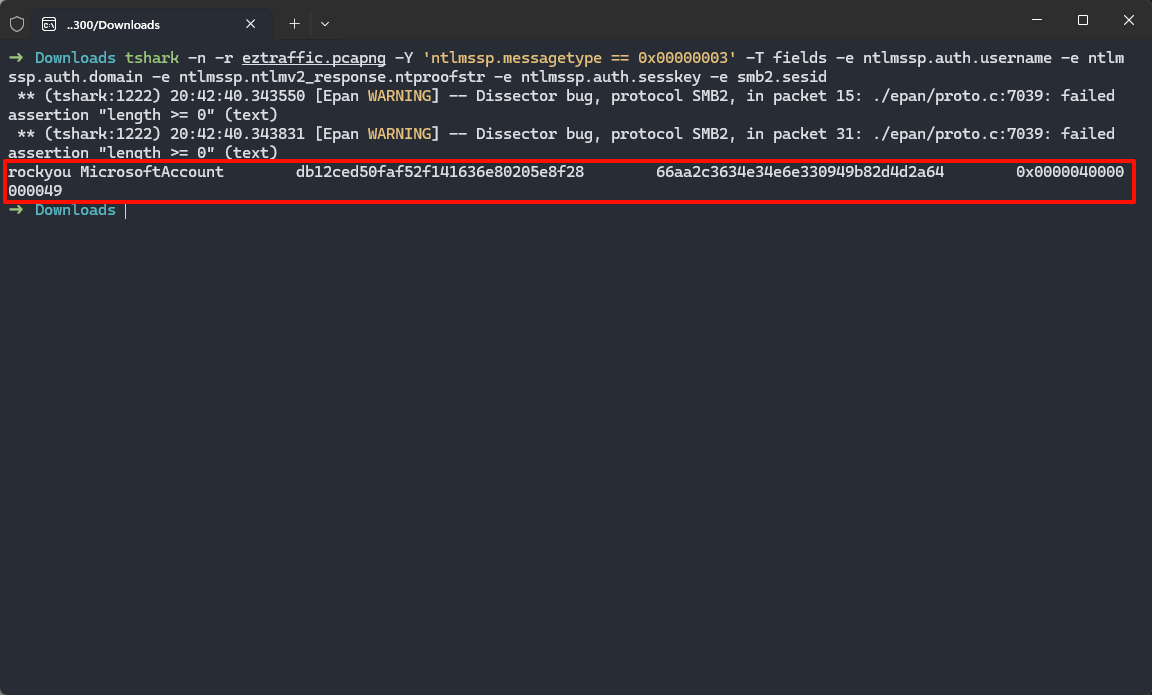
猜测是SMB协议传输的NTLM密码+五位数字掩码攻击获得flag,使用tshark导出
1
| tshark -n -r eztraffic.pcapng -Y 'ntlmssp.messagetype == 0x00000003' -T fields -e ntlmssp.auth.username -e ntlmssp.auth.domain -e ntlmssp.ntlmv2_response.ntproofstr -e ntlmssp.auth.sesskey -e smb2.sesid
|
![image]()
1
2
3
| username::domain:ServerChallenge:NTproofstring:modifiedntlmv2response
#根据这个格式找到下面的格式然后hashcat爆破
rockyou::MicrosoftAccount:4936df20962cae6d:db12ced50faf52f141636e80205e8f28:01010000000000003604281b951fdb017b4045aa008508eb0000000002001e00440042004500440036004200350041002d0035003100430032002d00340001001e00440042004500440036004200350041002d0035003100430032002d00340004004800640062006500640036006200350061002d0035003100630032002d0034003100650063002d0061006400380034002d0064006400320062003500370030006400350030003900360003004800640062006500640036006200350061002d0035003100630032002d0034003100650063002d0061006400380034002d00640064003200620035003700300064003500300039003600070008003604281b951fdb01060004000200000008003000300000000000000001000000002000008029a5d8256e5c2762f439df5c06f3bc411fb0faeb3a6fa52d9273c57b09f2d10a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e0031002e00380031000000000000000000
|
1
| hashcat -m 5600 hash.txt rockyou.txt
|
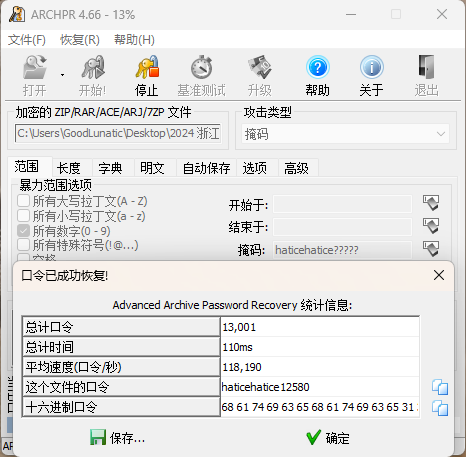
得到密码haticehatice,并进行掩码攻击
![image]()
得到解压密码后获得100张图片,在每张图片的Red 0通道中找到一张隐写的二维码,扫描二维码得到该图片在拼图中的顺序,写脚本完成拼图
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
| from PIL import Image
from pyzbar.pyzbar import decode
import os
def extract_lsb(imgname):
r = []
img = Image.open(imgname)
width,height = img.size
for x in range(width):
for y in range(height):
pixel = img.getpixel((x,y))
r.append(str(pixel[0] & 1))
bin_data = ''.join(r)
return bin_data
def bin2img(bin_data):
imgname = "tmp.png"
pixels = []
img = Image.new("RGB",(50,50))
for item in bin_data:
if item =='0':
pixels.append((0,0,0))
else :
pixels.append((255,255,255))
img.putdata(pixels)
img = img.resize((500,500))
img.save(imgname)
return imgname
def read_qrcode(imgname):
img = Image.open(imgname)
decode_data = decode(img)
res = decode_data[0].data.decode()
os.remove(imgname)
return res
def rename_img():
filenames = os.listdir("./final_out")
for filename in filenames:
try:
src_img = "./final_out/"+filename
bin_data = extract_lsb(src_img)
imgname = bin2img(bin_data)
res = read_qrcode(imgname)
dst_img = f"./final_out/{res}.png"
os.rename(src_img,dst_img)
print(f"[+] {src_img} ===> {dst_img} down!!!")
except:
print(f"[-] {src_img} Error!!!")
def merge_img():
cols = 10
rows = 10
img_list = []
new_img = Image.new("RGB",(500,500))
for i in range(1,101):
img = Image.open(f"./final_out/{i}.png")
img_list.append(img)
for y in range(rows):
for x in range(cols):
idx = y * cols + x
img = img_list[idx]
x_offset = x * 50
y_offset = y * 50
new_img.paste(img,(x_offset,y_offset))
new_img.save("flag.png")
if __name__ == "__main__":
merge_img()
|
![image]()